TryHackMe - Takeover
This challenge revolves around subdomain enumeration
Introduction
We have a little introduction text:
Hello there,
I am the CEO and one of the co-founders of futurevera.thm. In Futurevera, we believe that the future is in space. We do a lot of space research and write blogs about it. We used to help students with space questions, but we are rebuilding our support.
Recently blackhat hackers approached us saying they could takeover and are asking us for a big ransom. Please help us to find what they can takeover.
Our website is located at https://futurevera.thm
Hint: Don’t forget to add the 10.10.207.60 in /etc/hosts for futurevera.thm
Adding URL to /etc/hosts
Let’s add our IP to /etc/hosts file so we can access the web via URL
1
echo "10.10.207.60 futurevera.thm" | sudo tee -a /etc/hosts
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
nmap -T4 -n -sC -sV -Pn -p- 10.10.207.60
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b0:66:60:93:3a:bf:b7:e3:a9:3d:47:af:33:1d:9b:46 (RSA)
| 256 1a:38:12:53:7d:94:23:72:59:36:1a:da:77:b2:9b:1c (ECDSA)
|_ 256 9d:d0:92:e7:54:ec:b0:80:c5:29:f1:1d:a1:e7:92:76 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Did not follow redirect to https://futurevera.thm/
|_http-server-header: Apache/2.4.41 (Ubuntu)
443/tcp open ssl/http Apache httpd 2.4.41 ((Ubuntu))
| ssl-cert: Subject: commonName=futurevera.thm/organizationName=Futurevera/stateOrProvinceName=Oregon/countryName=US
| Not valid before: 2022-03-13T10:05:19
|_Not valid after: 2023-03-13T10:05:19
|_http-title: FutureVera
|_http-server-header: Apache/2.4.41 (Ubuntu)
| tls-alpn:
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Open ports:
22/tcp
80/tcp
443/tcp
Subdomains
Let’s check for subdomains using ffuf
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(rene㉿kali)-[~]
└─$ ffuf -H "Host: FUZZ.futurevera.thm" -u https://10.10.207.60 -w /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt -fs 0,4605
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : https://10.10.207.60
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt
:: Header : Host: FUZZ.futurevera.thm
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 0,4605
________________________________________________
blog [Status: 200, Size: 3838, Words: 1326, Lines: 81, Duration: 43ms]
support [Status: 200, Size: 1522, Words: 367, Lines: 34, Duration: 42ms]
Let’s add those subdomains to our /etc/hosts file
1
2
echo "10.10.207.60 blog.futurevera.thm" | sudo tee -a /etc/hosts
echo "10.10.207.60 support.futurevera.thm" | sudo tee -a /etc/hosts
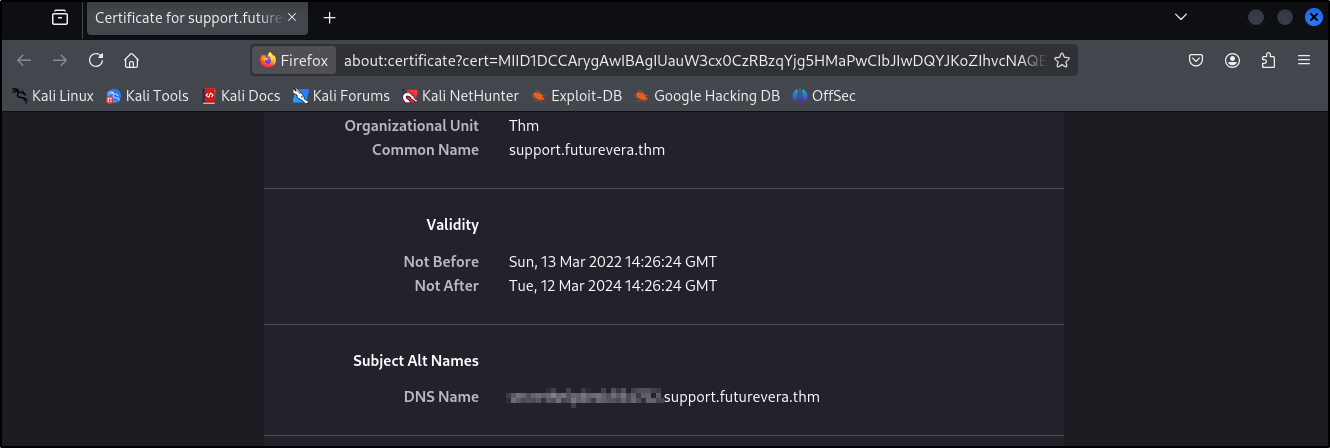
After visiting support subdomain and inspecting SSL certificate we can see some secret subdomain:
Let’s add the new subdomain to /etc/hosts file
1
echo "10.10.207.60 [CENSORED].support.futurevera.thm" | sudo tee -a /etc/hosts
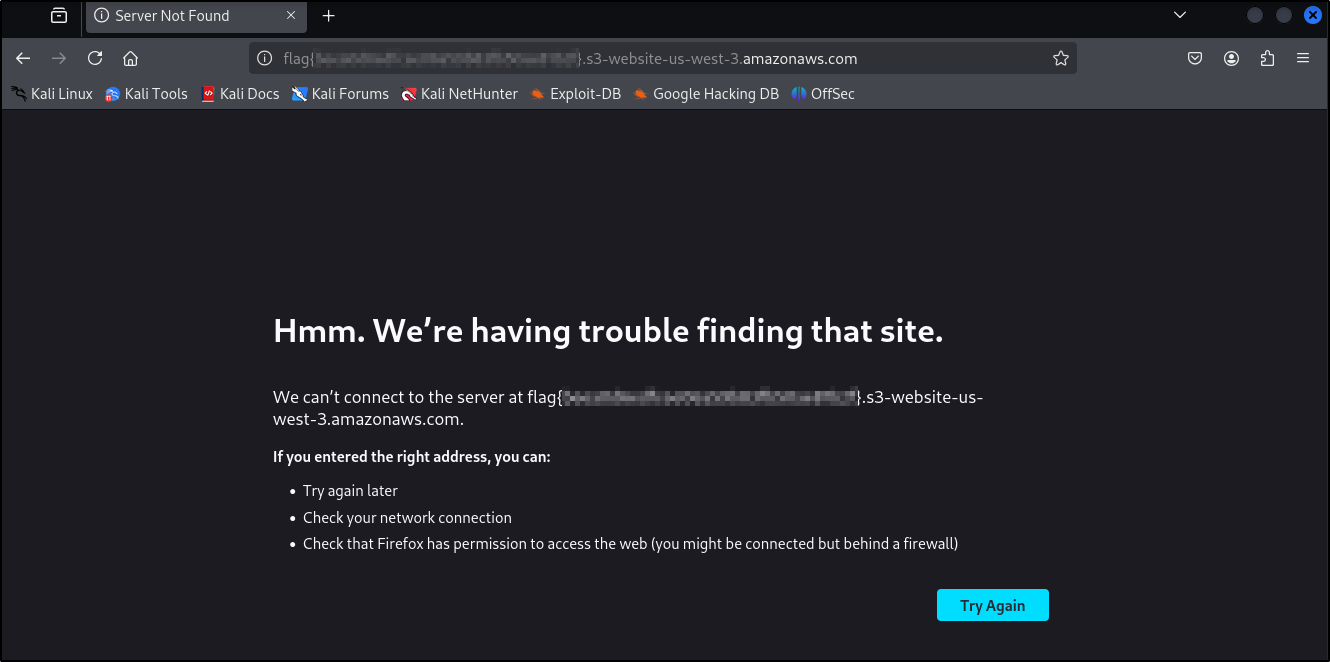
Flag
After adding and visiting the new subdomain, error message appears with the flag
Pretty quick room and good practice on how to use ffuf for subdomain enumeration.